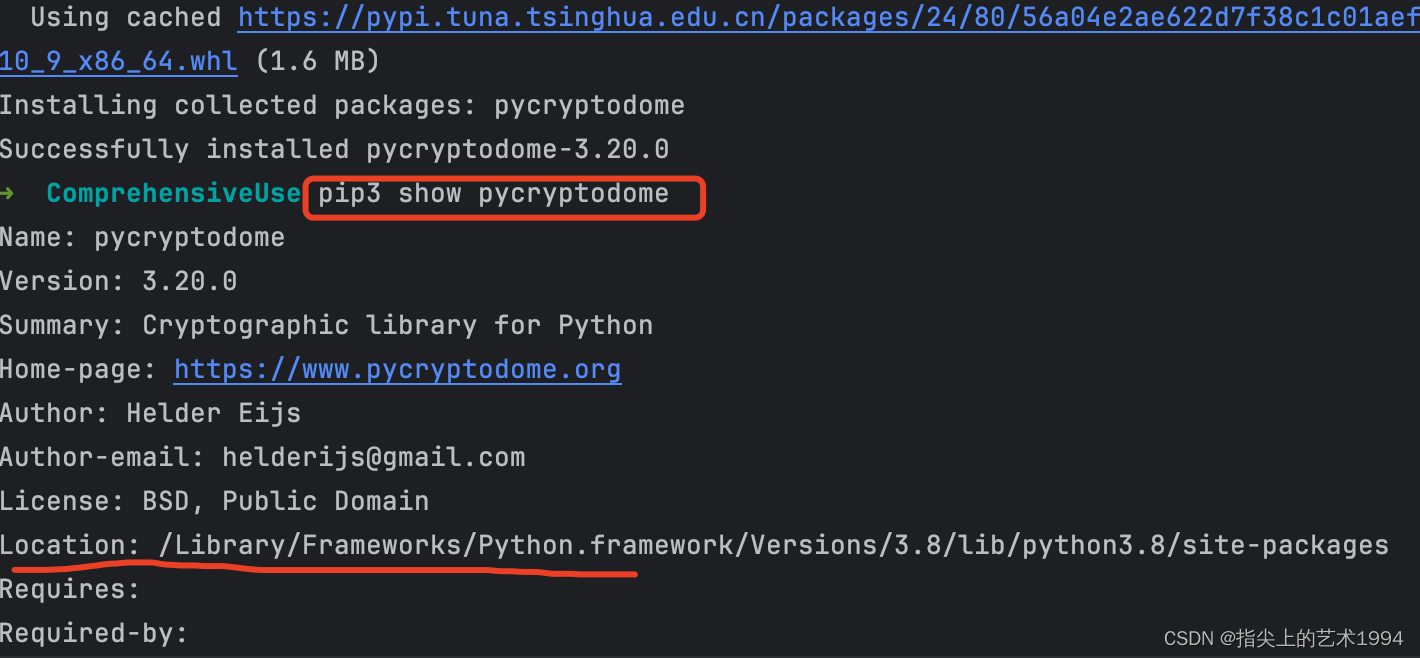
package main
import (
"crypto"
"crypto/rsa"
"crypto/sha256"
"crypto/x509"
"encoding/pem"
"errors"
"fmt"
)
func ParseRsaPublicKeyFromPemStr(pubPEM string) (*rsa.PublicKey, error) {
block, _ := pem.Decode([]byte(pubPEM))
if block == nil {
return nil, errors.New("failed to parse PEM block containing the key")
}
pub, err := x509.ParsePKCS1PublicKey(block.Bytes)
if err != nil {
return nil, err
}
return pub, nil
// switch pub := pub.(type) {
// case *rsa.PublicKey:
// return pub, nil
// default:
// break // fall through
// }
// return nil, errors.New("Key type is not RSA")
}
func main() {
// The GenerateKey method takes in a reader that returns random bits, and
// the number of bits
// privateKey, err := rsa.GenerateKey(rand.Reader, 2048)
// if err != nil {
// panic(err)
// }
// The public key is a part of the *rsa.PrivateKey struct
// publicKey := privateKey.PublicKey
publicKey, err := ParseRsaPublicKeyFromPemStr(`-----BEGIN RSA PUBLIC KEY-----
MIIBxxxxxx
-----END RSA PUBLIC KEY-----`)
if err != nil {
panic(err)
}
// // use the public and private keys
// // ...
// // https://play.golang.org/p/tldFUt2c4nx
// modulusBytes := base64.StdEncoding.EncodeToString(privateKey.N.Bytes())
// privateExponentBytes := base64.StdEncoding.EncodeToString(privateKey.D.Bytes())
// fmt.Println(modulusBytes)
// fmt.Println(privateExponentBytes)
// fmt.Println(publicKey.E)
// encryptedBytes, err := rsa.EncryptOAEP(
// sha256.New(),
// rand.Reader,
// &publicKey,
// []byte("super secret message111"),
// nil)
// if err != nil {
// panic(err)
// }
// fmt.Println("encrypted bytes: ", encryptedBytes)
// // The first argument is an optional random data generator (the rand.Reader we used before)
// // we can set this value as nil
// // The OEAPOptions in the end signify that we encrypted the data using OEAP, and that we used
// // SHA256 to hash the input.
// decryptedBytes, err := privateKey.Decrypt(nil, encryptedBytes, &rsa.OAEPOptions{Hash: crypto.SHA256})
// if err != nil {
// panic(err)
// }
// // We get back the original information in the form of bytes, which we
// // the cast to a string and print
// fmt.Println("decrypted message: ", string(decryptedBytes))
msg := []byte(`{"user_agent":"test"}`)
// // Before signing, we need to hash our message
// // The hash is what we actually sign
msgHash := sha256.New()
_, err = msgHash.Write(msg)
if err != nil {
panic(err)
}
msgHashSum := msgHash.Sum(nil)
// // In order to generate the signature, we provide a random number generator,
// // our private key, the hashing algorithm that we used, and the hash sum
// // of our message
// signature, err := rsa.SignPSS(rand.Reader, privateKey, crypto.SHA256, msgHashSum, nil)
// if err != nil {
// panic(err)
// }
signature := []byte{27, 79, , 8}
// To verify the signature, we provide the public key, the hashing algorithm
// the hash sum of our message and the signature we generated previously
// there is an optional "options" parameter which can omit for now
err = rsa.VerifyPSS(publicKey, crypto.SHA256, msgHashSum, signature, nil)
if err != nil {
fmt.Println("could not verify signature: ", err)
return
}
// If we don't get any error from the `VerifyPSS` method, that means our
// signature is valid
fmt.Println("signature verified")
}
参考:
https://gist.github.com/sohamkamani/08377222d5e3e6bc130827f83b0c073e
原文地址:https://blog.csdn.net/shelutai/article/details/134692786
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。
如若转载,请注明出处:http://www.7code.cn/show_10389.html
如若内容造成侵权/违法违规/事实不符,请联系代码007邮箱:suwngjj01@126.com进行投诉反馈,一经查实,立即删除!
主题授权提示:请在后台主题设置-主题授权-激活主题的正版授权,授权购买:RiTheme官网
声明:本站所有文章,如无特殊说明或标注,均为本站原创发布。任何个人或组织,在未征得本站同意时,禁止复制、盗用、采集、发布本站内容到任何网站、书籍等各类媒体平台。如若本站内容侵犯了原著者的合法权益,可联系我们进行处理。