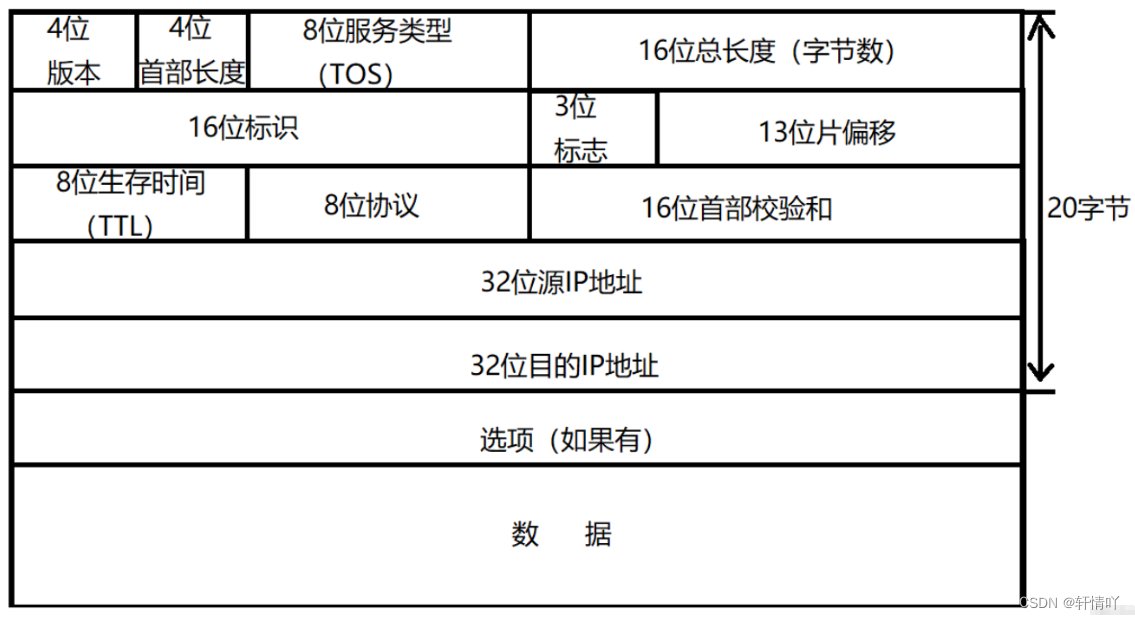
通过XFF地址动态限制访问
方案特点:
- 无需reload
- API管理
NGINX PLUS的KEYVAL是可以通过API进行管理的内部可持久化kv存储。
KEYVAL查找XFF地址是否在黑白名单中,来实现访问控制。
列表格式:
“10.0.0.1”: “0”,
“10.0.0.4”: “0”,
“10.0.0.2”: “1”,
“10.0.0.3”: “0”
动态黑白名单限制配置
http {
map $http_x_forwarded_for $client_ip {
“~(?P<ip>d+.d+.d+.d+)” $ip;
default “255.255.255.255”; #如果XFF地址格式错误,定义为特殊地址
}
keyval_zone zone=one:2m state=/var/lib/nginx/state/one.keyval;
keyval $client_ip $target zone=one; #用client_ip查找IP,匹配后赋值给$target
}
if ($target != 1) #不为1则禁止访问。 定义1为白名单标记
{
return 403 “you can‘t access“; }
proxy_pass http://192.168.145.130:800/;
}
}
测试禁止IP访问
curl -H “X-Forwarded-For: 11.0.0.1″ http://192.168.145.130:8888/example
![]()
命令行查看黑白名单
curl -X GET –s http://192.168.145.130:8888/api/7/http/keyvals/one | jq
{
“10.0.0.1”: “0”,
“10.0.0.4”: “0”,
“10.0.0.2”: “1”,
“10.0.0.3”: “0”
}
浏览器查看黑白名单

初次创建记录
curl -X POST –d ‘{“10.0.0.1″:”1”, “10.0.0.2”:”1″, “10.0.0.3”:”1″}’ –s http://192.168.145.130:8888/api/7/http/keyvals/one
追加记录
curl -X POST –d ‘{“20.0.0.1”: “1” }’ –s http://192.168.145.130:8888/api/7/http/keyvals/one
修改记录
curl -X PATCH –d ‘{“20.0.0.1”: “0” }’ –s http://192.168.145.130:8888/api/7/http/keyvals/one
删除所有记录
curl -X DELETE –s http://192.168.145.130:8888/api/7/http/keyvals/one
- NGINX管理方案
新建NGINX
个别黑白名单管理
批量黑白名单管理
参考:
- K8S架构下配置
-
DOCKFILE中禁止容器携带配置文件 && rm -rf /etc/nginx/nginx.conf && rm -rf /etc/nginx/conf.d/default.conf Deployment配置 apiVersion: apps/v1 kind: Deployment metadata: name: ng-deployment namespace: ns1 labels: app: nginx-plus spec: replicas: 1 selector: matchLabels: app: nginx-plus template: metadata: labels: app: nginx-plus spec: containers: - name: xxxxxx resources: limits: cpu: "1" memory: 512Mi requests: cpu: "2" memory: 1024Mi image: xxxxxx imagePullPolicy: IfNotPresent ports: - name: http containerPort: 80 - name: api containerPort: 8888 livenessProbe: failureThreshold: 3 httpGet: path: /nginx-health port: 80 initialDelaySeconds: 10 periodSeconds: timeoutSeconds: 2 readinessProbe: failureThreshold: 3 httpGet: path: /nginx-health port: 80 periodSeconds: 5 timeoutSeconds: 2 volumeMounts: - mountPath: /etc/nginx/conf.d readOnly: true name: nginx-config-per-svc volumes: - name: nginx-config-per-svc configMap: name: nginx-config-per-svc - NGINX PLUS配置
-
load_module modules/ngx_http_js_module.so; user nginx; worker_processes auto; error_log /var/log/nginx/error.log notice; pid /var/run/nginx.pid; events { worker_connections 1024; } http { include conf/mime.types; default_type application/default_type; log_format main '$remote_addr - $remote_user [$time_local] ' '"$request" $status $bytes_sent ' '"$http_referer" "$http_user_agent" ' '"$gzip_ratio"'; log_format download '$remote_addr - $remote_user [$time_local] "$request" ' '$status "$request_body" $body_bytes_sent "$http_referer" ' '"$http_user_agent" "$http_x_forwarded_for"'; access_log /var/log/nginx/access.log download; client_header_timeout 3m; client_body_timeout 3m; send_timeout 3m; client_header_buffer_size 1k; large_client_header_buffers 4 4k; gzip on; gzip_min_length 1100; gzip_buffers 4 8k; gzip_types text/plain; output_buffers 1 32k; postpone_output 1460; sendfile on; tcp_nopush on; tcp_nodelay on; send_lowat 12000; keepalive_timeout 75 20; lingering_time 30; lingering_timeout 10; reset_timedout_connection on; fastcgi_connect_timeout 300; fastcgi_send_timeout 300; fastcgi_read_timeout 300; fastcgi_buffer_size 64k; fastcgi_buffers 4 64k; fastcgi_busy_buffers_size 128k; fastcgi_temp_file_write_size 128k; map $http_x_forwarded_for $client_ip { "~(?P<ip>d+.d+.d+.d+)" $ip; "~(?P<ip>[^;]+)" $ip; default "255.255.255.255"; } keyval_zone zone=one:2m state=one.keyval; keyval $client_ip $target zone=one;
原文地址:https://blog.csdn.net/very_99/article/details/130043318
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。
如若转载,请注明出处:http://www.7code.cn/show_49440.html
如若内容造成侵权/违法违规/事实不符,请联系代码007邮箱:suwngjj01@126.com进行投诉反馈,一经查实,立即删除!