上一篇为大家详细介绍了tekton – pipeline,由于里面涉及到的概念比较多,因此需要好好消化下。同样,今天在特别为大家分享下tekton – Trigger以及案例演示,希望可以给大家提供一种思路哈。
1. Tekton Trigger
Trigger 组件就是用来解决这个触发问题的,它可以从各种来源的事件中检测并提取需要信息,然后根据这些信息来创建 TaskRun 和 PipelineRun,还可以将提取出来的信息传递给它们以满足不同的运行要求。
Tekton Trigger中有6类对象,分别是:
- EventListener:事件监听器,是外部事件的入口 ,通常需要通过HTTP方式暴露,以便于外部事件推送,比如配置Gitlab的Webhook。
- Trigger:指定当 EventListener 检测到事件发生时会发生什么,它会定义 TriggerBinding、TriggerTemplate 以及可选的 Interceptor。
- TriggerTemplate:用于模板化资源,根据传入的参数实例化 Tekton 对象资源,比如 TaskRun、PipelineRun等。
- TriggerBinding:用于捕获事件中的字段并将其存储为参数,然后会将参数传递给 TriggerTemplate。
- ClusterTriggerBinding:和 TriggerBinding 相似,用于提取事件字段,不过它是集群级别的对象。
- Interceptors:拦截器,在 TriggerBinding 之前运行,用于负载过滤、验证、转换等处理,只有通过拦截器的数据才会传递给TriggerBinding。
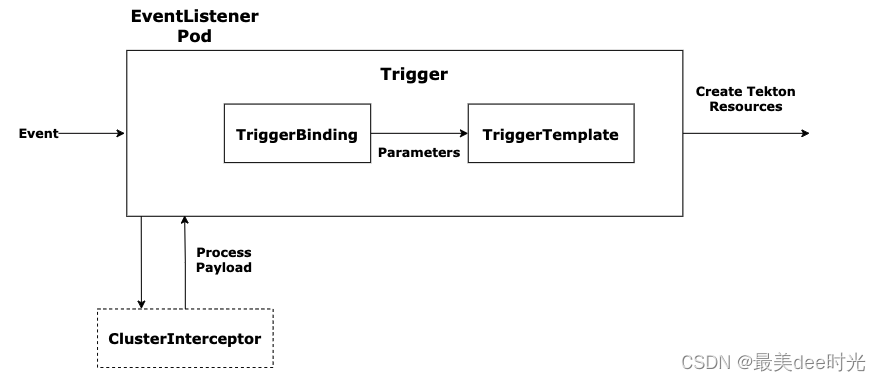
2. 工作流程
-
step1:EventListener 用于监听外部事件(具体触发方式为 http),外部事件产生后被 EventListener 捕获,然后进入处理过程。
-
step2:首先会由 Interceptors 来进行处理(如果有配置 interceptor 的话),对负载过滤、验证、转换等处理,类似与 http 中的 middleware。
-
step3:Interceptors 处理完成后无效的事件就会被直接丢弃,剩下的有效事件则交给 TriggerBinding 处理,
-
step4:TriggerBinding 实际上就是从事件内容中提取对应参数,然后将参数传递给 TriggerTemplate。
-
step5:TriggerTemplate 则根据预先定义的模版以及收到的参数创建 TaskRun 或者 PipelineRun 对象。
-
step6:TaskRun 或者 PipelineRun 对象创建之后就会触发对应 task 或者 pipeline 运行,整个流程就全自动了。
3. 安装trigger和interceptors
# install reigger
kubectl apply --filename https://storage.googleapis.com/tekton-releases/triggers/latest/release.yaml
# install interceptors
kubectl apply --filename https://storage.googleapis.com/tekton-releases/triggers/latest/interceptors.yaml
# monitor
kubectl get pods --namespace tekton-pipelines --watch
4. 案例
案例: gitlab跳代码触发tekton
step1: 创建task – 拉取代码
同pipeline案例2
step2: 创建task – 构建代码
同pipeline案例2
step3: 创建task – 打包镜像
task-package.yaml
apiVersion: tekton.dev/v1beta1
kind: Task
metadata:
name: package-2
spec:
workspaces:
- name: source # 名称
params:
- name: image_dest
type: string
default: "registry.ap-southeast-1.aliyuncs.com/my_image_repo"
- name: sha
type: string
default: "latest"
- name: DockerfilePath
type: string
default: Dockerfile
- name: Context
type: string
default: .
- name: project_name
type: string
default: "test"
steps:
- name: package
image: docker:stable
workingDir: $(workspaces.source.path)
script: |
#/usr/bin/env sh
Tag=$(params.sha)
tag=${Tag:0:6}
docker login registry.ap-southeast-1.aliyuncs.com
docker build -t $(params.image_dest)/$(params.project_name):${tag} -f $(params.DockerfilePath) $(params.Context)
docker push $(params.image_dest)/$(params.project_name):${tag}
volumeMounts:
- name: dockersorck
mountPath: /var/run/docker.sock
volumes:
- name: dockersorck
hostPath:
path: /var/run/docker.sock
step4: 创建pipeline
pipeline.yaml
apiVersion: tekton.dev/v1beta1
kind: Pipeline
metadata:
name: clone-build-push-2
spec:
description: |
This pipeline clones a git repo, builds a Docker image with Kaniko and
pushes it to a registry
params:
- name: repo-url
type: string
- name: sha
type: string
- name: project_name
type: string
- name: version
type: string
workspaces:
- name: shared-data
tasks:
# 拉取代码
- name: fetch-source
taskRef:
name: git-clone
workspaces:
- name: output
workspace: shared-data
params:
- name: url
value: $(params.repo-url)
- name: revision
value: $(params.version)
# 打包
- name: build-code
taskRef:
name: build-2
workspaces:
- name: source
workspace: shared-data
runAfter:
- fetch-source
# 构建并推送镜像
- name: package-image
runAfter: ["build-code"]
taskRef:
name: package-2
workspaces:
- name: source
workspace: shared-data
params:
- name: sha
value: $(params.sha)
- name: project_name
value: $(params.project_name)
step5: 创建pipelinerun
pipelinerun.yaml
apiVersion: tekton.dev/v1beta1
kind: PipelineRun
metadata:
generateName: clone-build-push-run-
#name: clone-build-push-run
spec:
serviceAccountName: gitlab-sa
pipelineRef:
name: clone-build-push-2
podTemplate:
securityContext:
fsGroup: 65532
workspaces:
- name: shared-data
volumeClaimTemplate:
spec:
accessModes:
- ReadWriteOnce
resources:
requests:
storage: 128Mi
params:
- name: repo-url
value: git@jihulab.com:cs-test-group1/kxwang/test.git #https://jihulab.com/cs-test-group1/kxwang/test.git
- name: sha
value: bchdsvhj12312312312241421
# - name: image_tag
# value: v2
- name: version
value: refs/heads/master
- name: project_name
value: wkx
step6: 创建事件监听器
EventListener.yaml
apiVersion: triggers.tekton.dev/v1alpha1
kind: EventListener
metadata:
name: gitlab-listener # 该事件监听器会创建一个名为el-gitlab-listener的Service对象
namespace: default
spec:
resources:
kubernetesResource:
serviceType: NodePort
serviceAccountName: gitlab-sa
triggers:
- name: gitlab-push-events-trigger
interceptors:
- ref:
name: gitlab
params:
- name: secretRef # 引用 gitlab-secret 的 Secret 对象中的 secretToken 的值
value:
secretName: gitlab-webhook
secretKey: secretToken
- name: eventTypes
value:
- Push Hook # 只接收 GitLab Push 事件
bindings:
- ref: pipeline-binding
template:
ref: pipeline-template
step7: 创建TriggerBinding文件
TriggerBinding.yaml
apiVersion: triggers.tekton.dev/v1beta1
kind: TriggerBinding
metadata:
name: pipeline-binding
spec:
params:
- name: repo-url
value: $(body.repository.git_ssh_url)
- name: version
value: $(body.ref)
- name: sha
value: $(body.checkout_sha)
- name: project_name
value: $(body.project.name)
step8: 创建TriggerTemplate模版文件
TriggerTemplate.yaml
apiVersion: v1
kind: Secret
metadata:
name: gitlab-webhook
type: Opaque
stringData:
secretToken: '123456789'
[root@VM-0-14-centos class-4]# cat TriggerTemplate.yaml
apiVersion: triggers.tekton.dev/v1beta1
kind: TriggerTemplate
metadata:
name: pipeline-template
spec:
params:
- name: sha
- name: project_name
- name: version
- name: repo-url
resourcetemplates:
- apiVersion: tekton.dev/v1beta1
kind: PipelineRun
metadata:
generateName: clone-build-push-run-
spec:
serviceAccountName: gitlab-sa
pipelineRef:
name: clone-build-push-2
params:
- name: sha
value: $(tt.params.sha)
- name: version
value: $(tt.params.version)
- name: repo-url
value: $(tt.params.repo-url)
- name: project_name
value: $(tt.params.project_name)
workspaces:
- name: shared-data
volumeClaimTemplate:
spec:
accessModes:
- ReadWriteOnce
resources:
requests:
storage: 128Mi
step9: 创建sa
gitlab-sa.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: gitlab-sa
secrets:
- name: gitlab-auth
- name: gitlab-ssh
- name: docker-credentials
- name: gitlab-webhook
step10: 创建gitlab webhook的信息
secret-gitlab-webhook.yaml
apiVersion: v1
kind: Secret
metadata:
name: gitlab-webhook
type: Opaque
stringData:
secretToken: '123456789'
step11: 创建RBAC
rbac.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: gitlab-sa
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: triggers-gitlab-clusterrole
rules:
# Permissions for every EventListener deployment to function
- apiGroups: ["triggers.tekton.dev"]
resources: ["eventlisteners", "triggerbindings", "triggertemplates","clustertriggerbindings", "clusterinterceptors","interceptors","triggers"]
verbs: ["get","list","watch"]
- apiGroups: [""]
# secrets are only needed for Github/Gitlab interceptors, serviceaccounts only for per trigger authorization
resources: ["configmaps", "secrets", "serviceaccounts"]
verbs: ["get", "list", "watch"]
# Permissions to create resources in associated TriggerTemplates
- apiGroups: ["tekton.dev"]
resources: ["pipelineruns", "pipelineresources", "taskruns"]
verbs: ["create"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: triggers-gitlab-clusterrolebinding
subjects:
- kind: ServiceAccount
name: gitlab-sa
namespace: default
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: triggers-gitlab-clusterrolegitlab-sa.yaml
step12: gitlab创建webhook
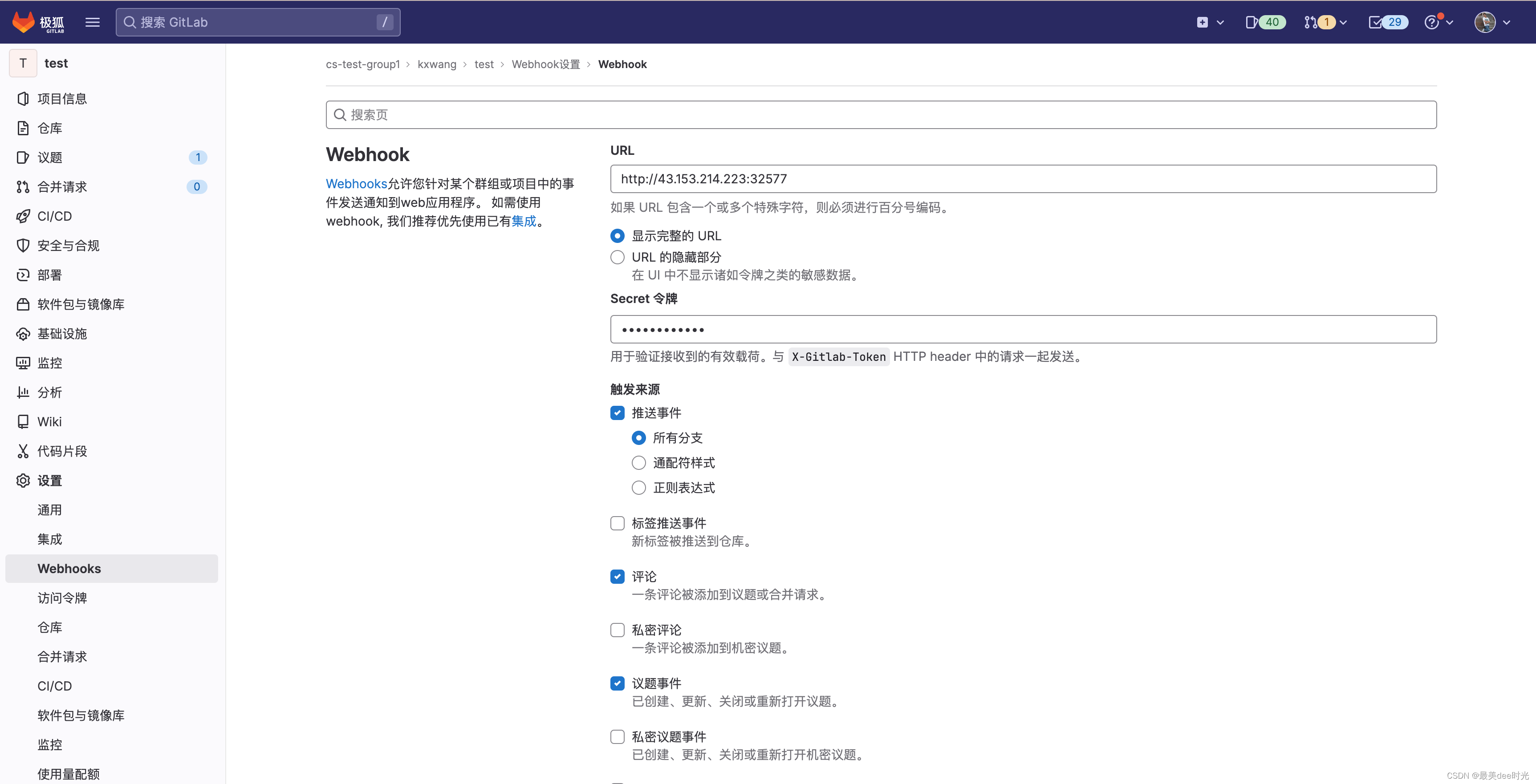
测试
界面提交下code
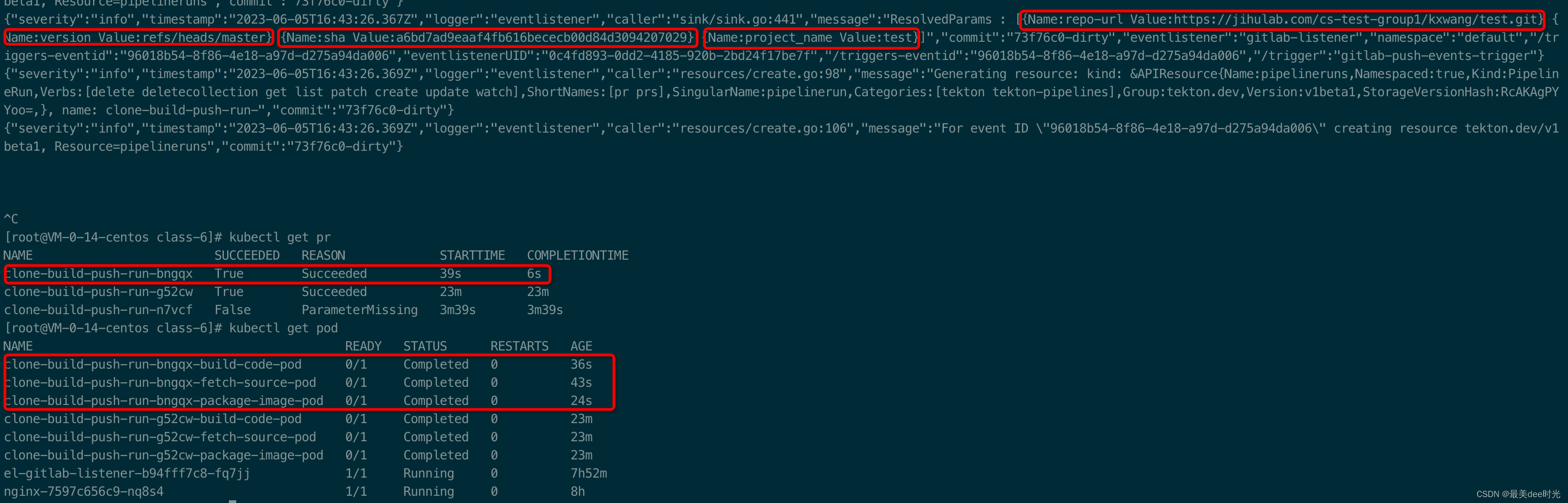
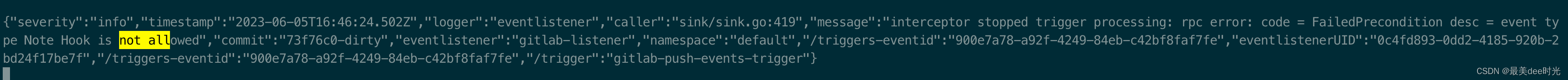
创建issue,验证拦截器规则
原文地址:https://blog.csdn.net/weixin_44729138/article/details/134818303
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。
如若转载,请注明出处:http://www.7code.cn/show_51011.html
如若内容造成侵权/违法违规/事实不符,请联系代码007邮箱:suwngjj01@126.com进行投诉反馈,一经查实,立即删除!