目录
一、SSH服务
1. ssh基础
SSH(Secure Shell)是一种安全通道协议,主要用来实现字符界面的远程登录、远程 复制等功能。SSH 协议对通信双方的数据传输进行了加密处理,其中包括用户登录时输入的用户口令,SSH 为建立在应用层和传输层基础上的安全协议。对数据进行压缩,加快传输速度。
ssh协议优点:
- 同时该协议具有加密输出,相较于telnet、FTP等明文传输方式更加安全
- 数据压缩的优点
软件包及相关路径:
- 服务名称:sshd
- 服务端主程序:/usr/sbin/sshd
- 服务端配置文件:/etc/ssh/sshd_config
- 客户端配置文件:/etc/ssh/ssh_config
[root@localhost ~]# cd /etc/ssh
[root@localhost ssh]# ls
moduli sshd_config ssh_host_ecdsa_key.pub ssh_host_ed25519_key.pub ssh_host_rsa_key.pub
ssh_config ssh_host_ecdsa_key ssh_host_ed25519_key ssh_host_rsa_key
#ssh_host_ecdsa_key.pub 通过ecdsa算法加密的公钥
#ssh_host_ecdsa_key 通过ecdsa算法加密的私钥2. 原理

① 客户端发起链接请求
② 服务端返回自己的公钥,以及一个会话ID(这一步客户端得到服务端公钥)
③ 客户端生成密钥对
④ 客户端用自己的公钥异或会话ID,计算出一个值Res,并用服务端的公钥加密
⑤ 客户端发送加密值到服务端,服务端用私钥解密,得到Res
⑥ 服务端用解密后的值Res异或会话ID,计算出客户端的公钥,服务端得到客户端公钥
⑦ 最终:双方各自持有三个秘钥,分别为自己的一对公、私钥,以及对方的公钥,之后的所有通讯都会被加密
对称加密
(1)概念
采用单钥密码系统的加密方法,同一个密钥可以同时用作信息的加密和解密,这种加密方法称为对称加密,由于其速度快,对称性加密通常在消息发送方需要加密大量数据时使用。
(2)特点
加密解密传输速度快,但是安全性较低,加密和解密使用同一个密钥
非对称加密
(1)概念
非对称加密算法需要两个密钥:公开密钥(publickey:简称公钥)和私有密钥(privatekey:简称私钥)。公钥与私钥是一对,如果用公钥对数据进行加密,只有用对应的私钥才能解密。因为加密和解密使用的是两个不同的密钥,所以这种算法叫作非对称加密算法。
(2)特点
密解密传输速度慢,但是安全性较高,加密和解密需要使用不同的密钥
如何确认连接的服务端是不是我们想要访问的?
提前记录服务端的公钥,下次连接时核对获得的公钥是否与需要的一致。
登录方法:
客户端:
[root@localhost ~]# ssh root@192.168.190.101
#默认使用22端口 root(登录对方的用户)加IP地址,首次登录会询问,并要求输入密码
The authenticity of host '192.168.190.101 (192.168.190.101)' can't be established.
ECDSA key fingerprint is SHA256:aIqKteFz37bh8tOF7A07YElsVqfHgBSbxwkKXK9dfks.
ECDSA key fingerprint is MD5:9c:5a:7f:ec:d9:0c:2a:b2:9d:9e:03:77:f3:87:36:d4.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.190.101' (ECDSA) to the list of known hosts.
root@192.168.190.101's password:
Last login: Sat Jan 13 14:26:09 2024 from 192.168.190.1
[root@localhost ~]# exit
登出
Connection to 192.168.190.101 closed.
[root@localhost .ssh]# cd
[root@localhost ~]# cd .ssh
[root@localhost .ssh]# ls
known_hosts
[root@localhost .ssh]# cat known_hosts
192.168.190.101 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBAGrNfplQ1uWAa7tuFe14mzHMtaAb6zKFG0phfTMPqJixfIWgoaIh0hHp8gvumMufYzF7JICVYDWTkFy3VIYVUU=
#获得的服务端公钥
服务端:
[root@localhost ssh]# cat ssh_host_ecdsa_key.pub
ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBAGrNfplQ1uWAa7tuFe14mzHMtaAb6zKFG0phfTMPqJixfIWgoaIh0hHp8gvumMufYzF7JICVYDWTkFy3VIYVUU=
#服务端公钥ssh选项:
ssh -l [远程主机用户名] [远程服务器主机名或IP地址] -p port
-l:-l 选项,指定登录名称。
[root@localhost ~]# ssh -l root 192.168.190.101
root@192.168.190.101's password:
Last login: Sat Jan 13 14:34:21 2024 from 192.168.190.100-p:-p 选项,指定登录端口(当服务端的端口非默认时,需要使用-p 指定端口进行登录)
服务端:
[root@localhost ~]# cd /etc/ssh
[root@localhost ssh]# vim sshd_config #修改服务端配置
17 Port 888 #指定登录端口号888
[root@localhost ssh]# systemctl stop firewalld.service
[root@localhost ssh]# setenforce 0
[root@localhost ssh]# systemctl restart sshd
客户端
[root@localhost ~]# ssh 192.168.190.101 -p 888
root@192.168.190.101's password:
Last login: Sat Jan 13 15:32:24 2024 from 192.168.190.101
[root@localhost ~]# w | grep 192.168.190.100
root pts/1 192.168.190.100 15:21 5.00s 0.12s 0.04s ssh 192.168.190.101 -p 888-t:跳板,当服务端无法直接访问时可以通过访问其他设备转接服务端
服务端:192.168.190.101
[root@localhost ssh]# iptables -A INPUT -s 192.168.190.100 -j REJECT
#模拟防火墙,丢弃来自192.168.190.100所有的流量包
客户端:192.168.190.100
[root@localhost ~]# ping 192.168.190.101
PING 192.168.190.101 (192.168.190.101) 56(84) bytes of data.
From 192.168.190.101 icmp_seq=1 Destination Port Unreachable
From 192.168.190.101 icmp_seq=2 Destination Port Unreachable #此时客户端无法ping通服务端
[root@localhost ~]# ssh 192.168.190.101
ssh: connect to host 192.168.190.101 port 22: Connection refused #拒绝访问
[root@localhost ~]# ssh -t 192.168.190.102 ssh -t 192.168.190.101
#通过102跳转到101
The authenticity of host '192.168.190.102 (192.168.190.102)' can't be established.
ECDSA key fingerprint is SHA256:pEW/xy589bfYuWl9zTchcXoKlgB/IILjpmhWvsDJsPU.
ECDSA key fingerprint is MD5:17:bb:91:f2:97:b0:58:73:ae:b2:d8:1b:56:24:83:c0.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.190.102' (ECDSA) to the list of known hosts.
root@192.168.190.102's password:
The authenticity of host '192.168.190.101 (192.168.190.101)' can't be established.
ECDSA key fingerprint is SHA256:aIqKteFz37bh8tOF7A07YElsVqfHgBSbxwkKXK9dfks.
ECDSA key fingerprint is MD5:9c:5a:7f:ec:d9:0c:2a:b2:9d:9e:03:77:f3:87:36:d4.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.190.101' (ECDSA) to the list of known hosts.
root@192.168.190.101's password:
Last login: Sat Jan 13 22:50:53 2024 from 192.168.190.1
[root@localhost ~]#
3. 服务端配置
3.1 常用配置项
[root@localhost ~]# vim /etc/ssh/sshd_config #服务端配置文件
17 #Port 22 #生产建议修改
19 #ListenAddress 0.0.0.0 #监听地址设置SSHD服务器绑定的IP 地址,0.0.0.0 表示侦听所有地址
37 #LoginGraceTime 2m #用来设定如果用户登录失败,在切断连接前服务器需要等待的时间,单位为秒
38 #PermitRootLogin yes #不允许root远程ssh登录,改为no即可
39 #StrictModes yes #检查.ssh/文件的所有者,权限等
40 #MaxAuthTries 6 #用来设置最大失败尝试登陆次数为6
41 #MaxSessions 10 #同一个连接最大会话
43 #PubkeyAuthentication yes #基于key验证
64 #PermitEmptyPasswords no #通过认证的秘钥来登陆
65 PasswordAuthentication yes #基于用户名和密码连接
115 #UseDNS no #禁用反向解析,内网改为no3.2 具体操作
3.2.1 修改默认端口号
[root@localhost ~]# vim /etc/ssh/sshd_config
17 Port 新端口号
3.2.2 禁止root用户登录
[root@localhost ~]# vim /etc/ssh/sshd_config
38 PermitRootLogin no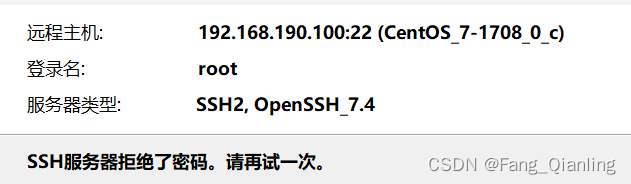
注意虽然阻止了root 但是普通用户可以使用su
[C:~]$ ssh fql@192.168.190.100
Connecting to 192.168.190.100:22...
Connection established.
To escape to local shell, press 'Ctrl+Alt+]'.
/usr/bin/xauth: file /home/fql/.Xauthority does not exist
[fql@localhost ~]$ su root
密码:
[root@localhost fql]# 修改pam认证模块,只允许wheel组用户可以使用su
[root@localhost ~]# vim /etc/pam.d/su
6 #auth required pam_wheel.so use_uid
#开启第6行,默认注释3.2.3 白名单列表
服务端:
[root@localhost ~]# vim /etc/ssh/sshd_config
140 AllowUsers fql@192.168.190.101 lisi
#只允许192.168.190.101访问服务端的fql用户;允许所有人访问服务端的lisi用户
[root@localhost ~]# systemctl restart sshd
客户端:
[root@localhost ~]# ssh fql@192.168.190.100
The authenticity of host '192.168.190.100 (192.168.190.100)' can't be established.
ECDSA key fingerprint is SHA256:6+8qeJTs9OwWCvFNtomXsQvrfb+no8F3moR0oliq7QU.
ECDSA key fingerprint is MD5:3b:d2:42:d9:c3:03:ba:ac:18:2c:e0:03:a3:c7:bd:ba.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.190.100' (ECDSA) to the list of known hosts.
fql@192.168.190.100's password:
[fql@localhost ~]$ exit #可以访问fql用户
登出
Connection to 192.168.190.100 closed.
[root@localhost ~]# ssh root@192.168.190.100
root@192.168.190.100's password:
Permission denied, please try again. #被拒绝访问
[root@localhost ~]# ssh lisi@192.168.190.100 #可以访问lisi用户
lisi@192.168.190.100's password:
[lisi@localhost ~]$ 3.2.4 黑名单列表
服务端:
[root@localhost ~]# vim /etc/ssh/sshd_config
141 DenyUsers lisi #拒绝所有人访问lisi用户
[root@localhost ~]# systemctl restart sshd
客户端:
[root@localhost ~]# ssh lisi@192.168.190.100
lisi@192.168.190.100's password:
Permission denied, please try again.注:如果同一个条件黑白名单都存在,执行黑名单条件
3.2.5 使用秘钥对及免交互验证登录
生成rsa算法密钥:
[root@localhost ~]# ssh-keygen #不指定加密算法直接回车
Generating public/private rsa key pair. #默认使用ras算法的加密方式
Enter file in which to save the key (/root/.ssh/id_rsa): #文件默认路径
Enter passphrase (empty for no passphrase): #给这个密钥设置密码(隐藏)
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:DA+e1rp8+dXI4HlV1Qkt48ESsiB1/KpYvxelRKKh6QI root@localhost.localdomain
The key's randomart image is:
+---[RSA 2048]----+
| ..o.o .o.o +|
| ..oooo = oo|
| = o.+ o + .|
| E + O o o . |
| . . + S + o . |
| . o o o * + |
| . + o.o * . |
| o oo. + |
| o. o+ |
+----[SHA256]-----+
[root@localhost ~]# cd .ssh
[root@localhost .ssh]# ls
id_rsa id_rsa.pub #生成了两个rsa算法的密钥
[root@localhost .ssh]#
传输密钥:
192.168.190.100:
[root@localhost .ssh]# ls
id_rsa id_rsa.pub known_hosts
[root@localhost .ssh]# ssh-copy-id -i ~/.ssh/id_rsa.pub 192.168.190.101
#将公钥传给192.168.190.101
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_rsa.pub"
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
root@192.168.190.101's password:
Permission denied, please try again.
root@192.168.190.101's password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh '192.168.190.101'"
and check to make sure that only the key(s) you wanted were added.
192.168.190.101:
[root@localhost ~]# cd .ssh
[root@localhost .ssh]# ls
authorized_keys known_hosts #已收到公钥验证登录:
[root@localhost .ssh]# ssh 192.168.190.101
Enter passphrase for key '/root/.ssh/id_rsa': #输入密钥密码
Last login: Sun Jan 14 22:00:14 2024 from 192.168.190.1为了保证安全,可以只使用密钥文件验证 :
[root@localhost .ssh]# vim /etc/ssh/sshd_config
43 PubkeyAuthentication yes
65 PasswordAuthentication no
[root@localhost .ssh]# systemctl restart sshd3.2.6 免交互式登录
[root@localhost .ssh]# ssh-agent bash #把sh-agent交给进程管理
[root@localhost .ssh]# ssh-add #把密码交给sh-agent
Enter passphrase for /root/.ssh/id_rsa: #输入密钥文件密码
Identity added: /root/.ssh/id_rsa (/root/.ssh/id_rsa)
[root@localhost .ssh]# ssh 192.168.190.101 #无需密码即可登录,重启后失效
Last login: Sun Jan 14 22:06:03 2024 from 192.168.190.1原文地址:https://blog.csdn.net/qq_64612585/article/details/135569290
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。
如若转载,请注明出处:http://www.7code.cn/show_57744.html
如若内容造成侵权/违法违规/事实不符,请联系代码007邮箱:suwngjj01@126.com进行投诉反馈,一经查实,立即删除!