预知
ingress实现https代理
创建证书 密钥
secrets保存密钥信息,部署pod时把secrets挂载到pod
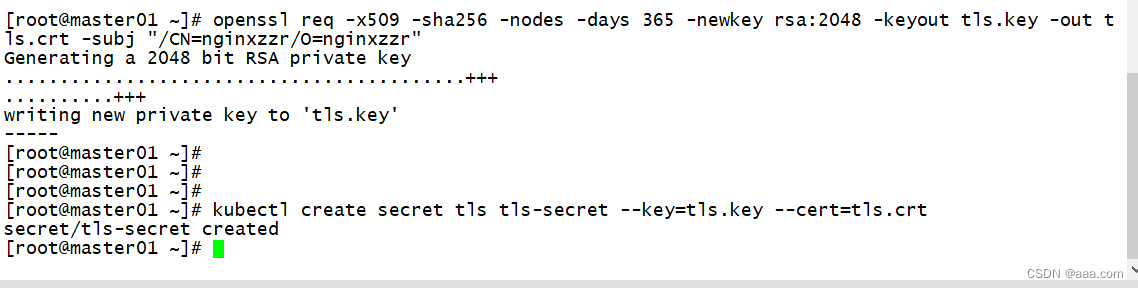
[root@master01 ~]# openssl req -x509 -sha256 -nodes -days 365 -newkey rsa:2048 -keyout tls.key -out.crt -subj "/CN=nginxzzr/O=nginxzzr"
req:生成证书文件的请求
x509:生成x.509自签名的证书
-sha256:表示生成的密钥不加密
-day 365:证书有效期365天
-newkey rsa:2048 :RSA密钥对,长度2048位。
-keyout tls.key -out.crt:密钥文件key 证书文件:crt
-subj "/CN=nginxzzr/O=nginxzzr":主题 , CN common name O;organization
kubectl create secret tls tls-secret --key=tls.key --cert=tls.crt
创建secret创建deployment,service,ingress的yaml资源
apiVersion: apps/v1
kind: metadata
metadata:
name: nginx-https
labels:
app: https
spec:
replicas: 3
selector:
matchLabels:
app: https
template:
metadata:
labels:
app: https
spec:
containers:
- name: nginx
image: nginx:1.22
---
apiVersion: v1
kind: Service
metadata:
name: nginx-svc
spec:
ports:
- port: 80
targetPort: 80
protocol: TCP
selector:
app: https
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: nginx-ingress-https
spec:
tls:
- hosts:
- www.123zzr.com
secretName: tls-secret
#加密的配置保存在ingress当中(请求---ingress-controller---ingress----service)。所以在ingress模块将加密文件导入
#在代理进行时,就要先验证密钥对,然后再把请求转发到service对应的pod
rules:
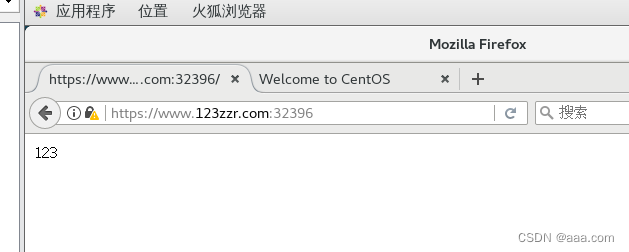
- host: www.123zzr.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: nginx-svc
port:
number: 80
wq
kubectl apply -f ingress-https.yaml
kubectl get pod
kubectl get svc -n ingress-nginx
vim /etc/hosts
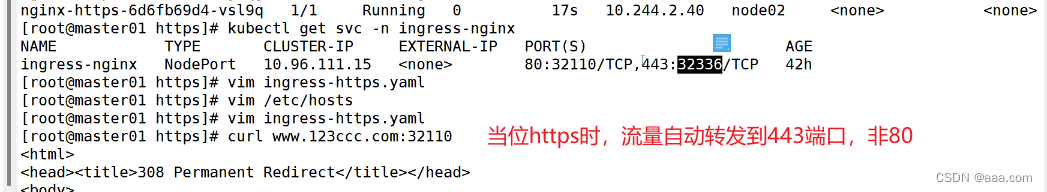
也可以实现负载均衡。
nginx的登录账号认证
cd /opt
cd https
mkdir basic-auth
cd basic-auth
yum -y install httpd
htpasswd -c auth zzr
123456
123456
//认证的文件名只能叫auth
ls
认证文件已经生成
kubectl create secret generic basic-auth --from-file=auth
kubectl describle secrets basic-auth
vim ingress.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-auth
annotations:
#开启认证模块
nginx.ingress.kubernets.io/auth-type: basic
#设置认证类型位basic,这是k8s自带的认证加密模块
nginx.ingress.kubernets.io/auth-secret: basic-auth
#把认证的加密模块导入ingress当中
nginx.ingress.kubernets.io/auth-realm: 'Authentication Required -zzr'
spec:
rules:
- hosts: www.zzr.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: nginx-svc
port:
number: 80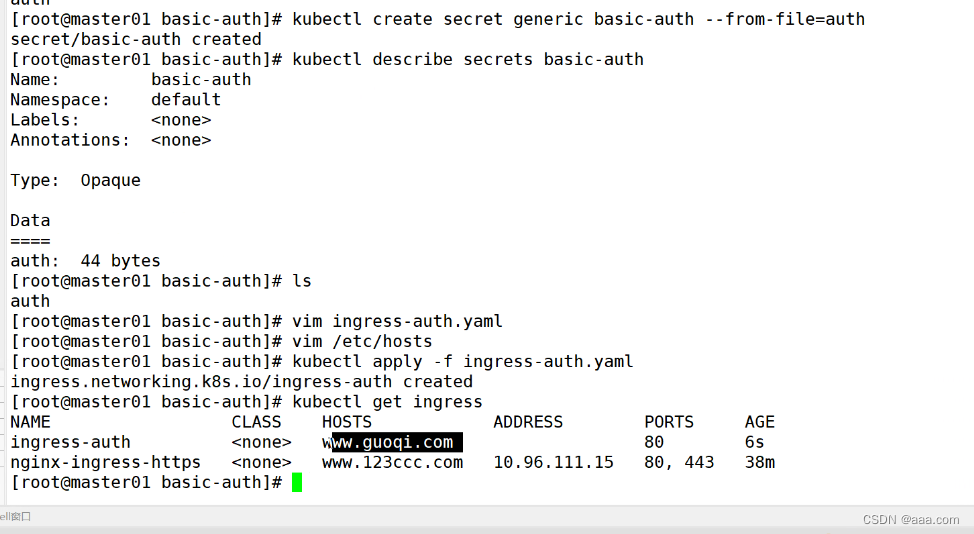
nginx重写
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: nginx-rewrite
annotations:
nginx.ingress.kubernetes.io/rewrite-target: https://www.123zzr.com:32396
spec:
rules:
- host: www.zzr.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: nginx-svc
port:
number: 80
vim /etc/hosts
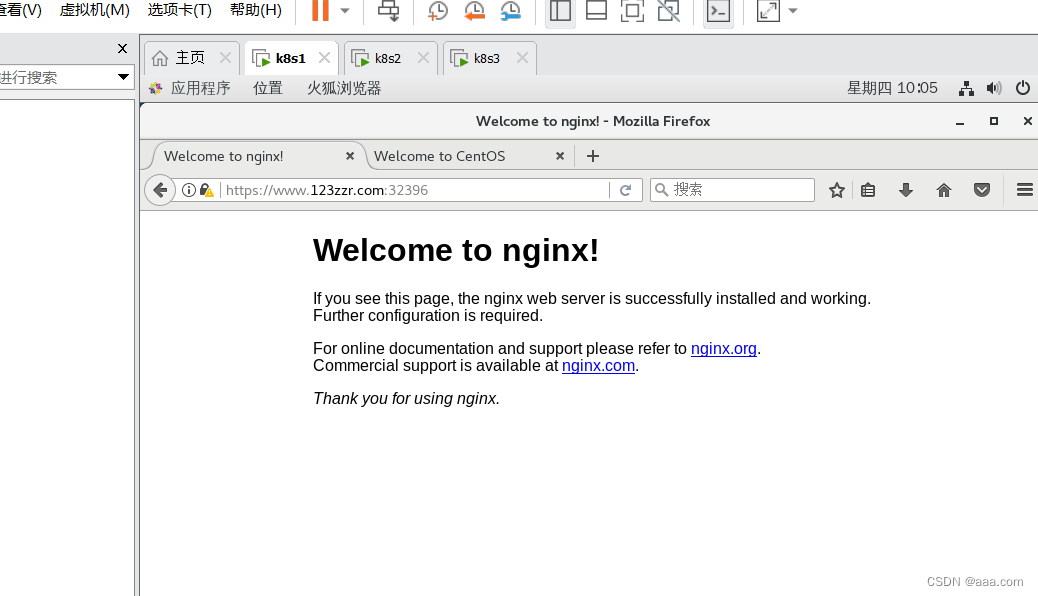
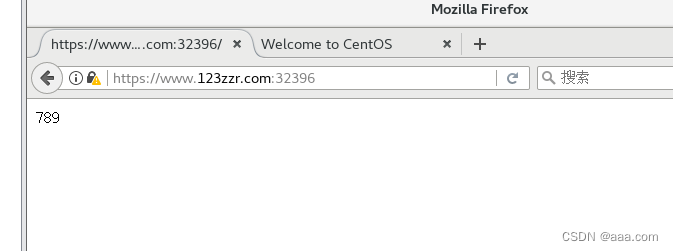
nginx-ingress-controller
traefik ingress controller
traefik 是一个为了让部署微服务更加快捷而诞生的一个http反向代理,负载均衡。
traefik设计时就能够实时的和k8s API交互,可以感知后端service和pod的变化,还可以自动更新配置和重载。
pod内 nginx 80 8081
traefik的部署方式:
daemonset
特点:优点,每个节点都会部署一个traefik,节点感知,可以自动发现,更新容器的配置。不需要手动重载。
缺点:资源占用,大型集群中,daemonset可能会运行多个traefik的实力,尤其是节点上不需要大量容器的情况下。没有办法扩缩容。
部署对外集群:对外的业务会经常变更,daemonset可以更好的,自动的发现服务配置变更
deployment:
优点:集中办公控制,可以使用少量的实例来运行处理整个集群的流量。更容易升级和维护。
缺点:deployment的负载均衡不会均分到每个节点。
无法感知容器内部配置的变化,所以得手动更新。
部署对内集群:对内的相对稳定,更新和变化也比较少,适合deployment
tarffic-type:internal 对内服务
traffic-type:external 对外服务
nignx-ingress和traefik-ingress区别
nginx-ingress 相对较慢
工作原理都一样,都是7层代理,都可以动态的更新配置,都可以自动发现服务。
traefik-ingress自动更新的重载更快,更方便
traefik的并发能力只有nginx-ingress的60%
演示deployment
cd /opt
mkdir traefik
cd traefik
wget https://gitee.com/mirrors/traefik/raw/v1.7/examples/k8s/traefik-deployment.yaml
wget https://gitee.com/mirrors/traefik/raw/v1.7/examples/k8s/traefik-rbac.yaml
wget https://gitee.com/mirrors/traefik/raw/v1.7/examples/k8s/traefik-ds.yaml
//daemonset
wget https://gitee.com/mirrors/traefik/raw/v1.7/examples/k8s/ui.yaml
kubectl apply -f traefik-rbac.yaml
kubectl apply -f traefik-ds.yaml
kubectl apply -f ui.yaml
vim traefik-
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-traefik
labels:
nginx: traefik
spec:
replicas: 3
selector:
matchLabels:
nginx: traefik
template:
metadata:
labels:
nginx: traefik
spec:
containers:
- name: nginx
image: nginx:1.22
---
apiVersion: v1
kind: Service
metadata:
name: nginx-traefik-svc1
spec:
ports:
- port: 80
targetPort: 80
protocol: TCP
selector:
nginx: traefik
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: nginx-traefik-test1
spec:
rules:
- host: www.zzrhj.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: nginx-traefik-svc1
port:
number: 80
wq
kubectl apply -f traefik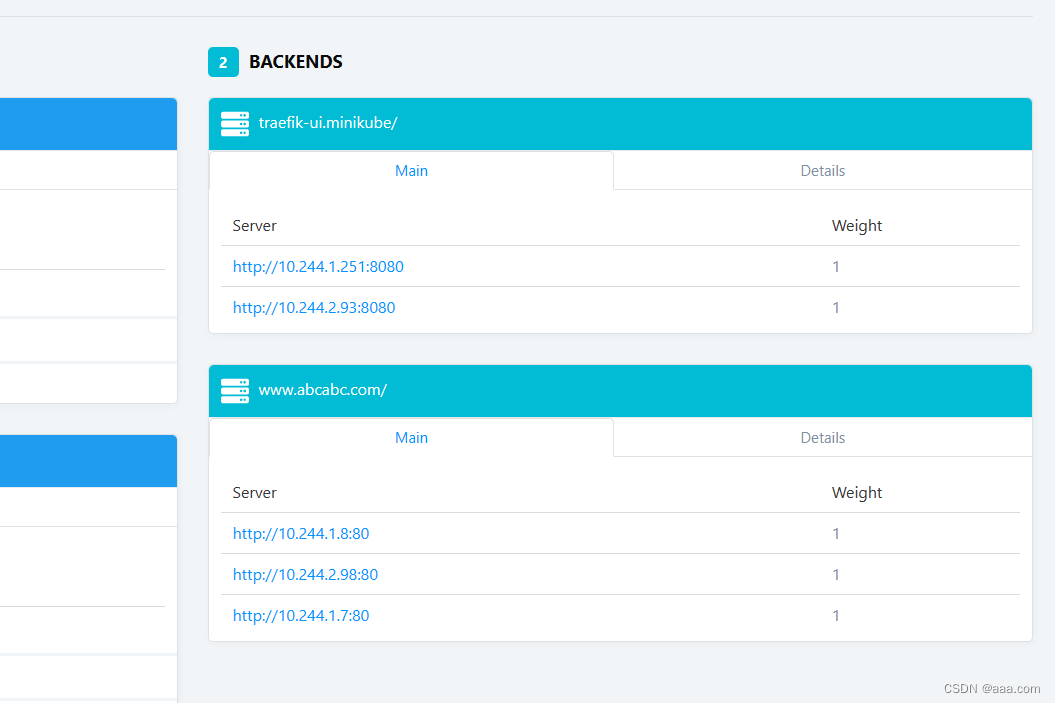
daemonset演示
cd /opt
mkdir traefik
cd traefik
wget https://gitee.com/mirrors/traefik/raw/v1.7/examples/k8s/traefik-rbac.yaml
wget https://gitee.com/mirrors/traefik/raw/v1.7/examples/k8s/traefik-ds.yaml
//daemonset
wget https://gitee.com/mirrors/traefik/raw/v1.7/examples/k8s/ui.yaml
kubectl apply -f traefik-rbac.yaml
kubectl apply -f traefik-ds.yaml
kubectl apply -f ui.yamlapiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-traefik
labels:
nginx: traefik
spec:
replicas: 3
selector:
matchLabels:
nginx: traefik
template:
metadata:
labels:
nginx: traefik
spec:
containers:
- name: nginx
image: nginx:1.22
volumeMounts:
- name: nginx-conf
mountPath: /etc/nginx
volumes:
- name: nginx-conf
configMap:
name: nginx-conf
---
apiVersion: v1
kind: Service
metadata:
name: nginx-traefik-svc1
spec:
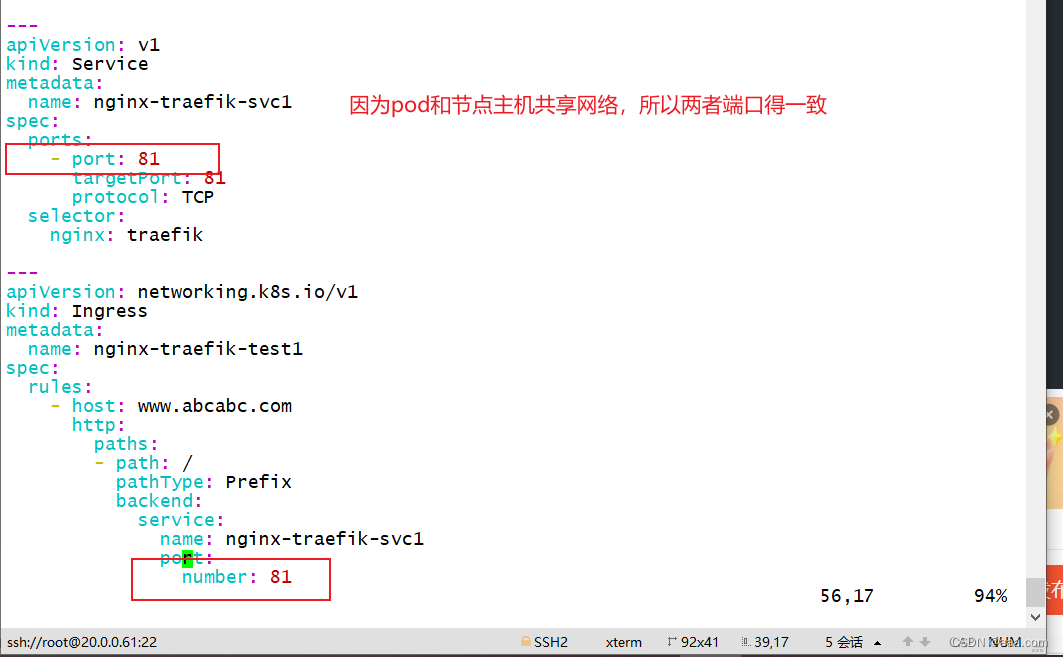
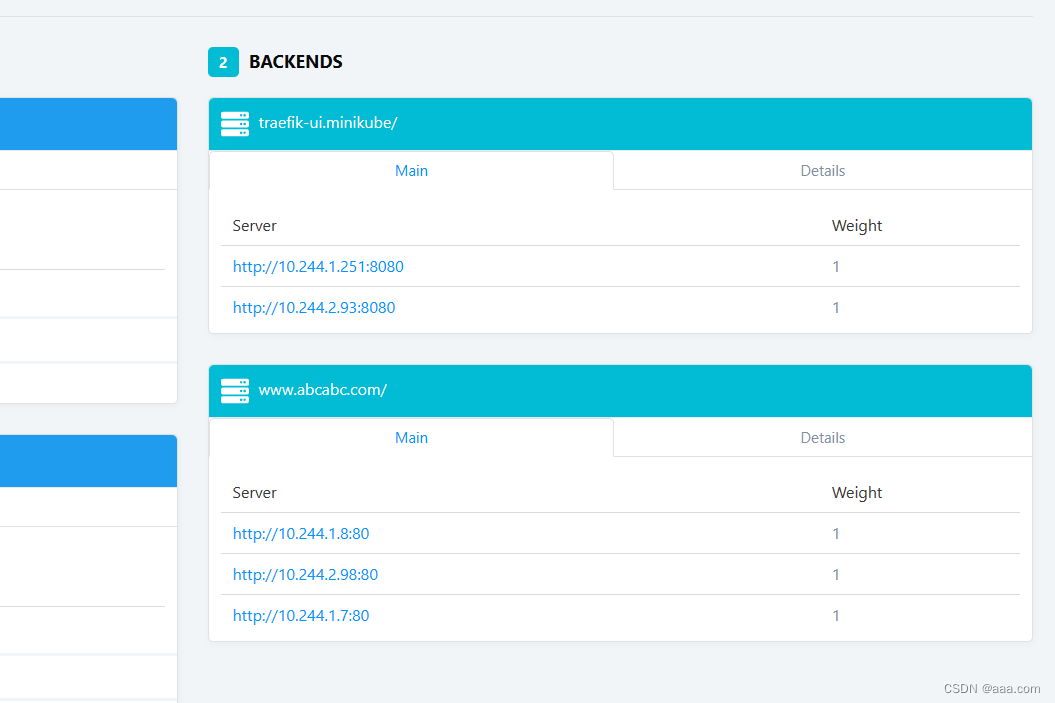
ports:
- port: 81
targetPort: 81
protocol: TCP
selector:
nginx: traefik
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: nginx-traefik-test1
spec:
rules:
- host: www.abcabc.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: nginx-traefik-svc1
port:
number: 81
ingress总结
ingress的类型:
nginx-ingress-controller
traefik-ingress-controller
这两个都是开源的控制器
nginx-ingress-controller控制器三种模式:
deployment+loadbalancer:公有云提供负载均衡的公网地址
daemonset+hostnetwork+nodeselector:和节点服务共享网络,一个节点一个controller pod。使用宿主机的端口性能最好,适合大并发
deployment+nodeport:最常见也是最常用,也是最简单的方法。但是性能不太好,多了一层nat地址转发。
适用于高并发、大集群使用
traefik-ingress-controller控制器模式:
daemonset:对外,开源自动更新容器配置。使用hostnetwork模式 使用节点网络
deployment:对内 无法自动更新配置。使用nodeport模式。
适用于小集群
https:
1.生成证书,密钥
2.创建secret,保存证书和密钥
3.创建ingress把secret导入。
加密认证:
-
htpasswd -c auth:认证文件只能是auth
-
创建ingress时指定认证的类型、导入密钥文件、最后加上密钥信息
-
定义ingress的规则
-
annotations: #开启认证模块的配置 nginx.ingress.kubernetes.io/auth-type: basic #设置认证类型为basic。是k8s自带的认证加密模块 nginx.ingress.kubernetes.io/auth-secret: basic-auth #把认证的加密模块导入到ingress当中 nginx.ingress.kubernetes.io/auth-realm: 'Authentication Required-zyg' #设置认证窗口的提示信息。
nginx重定向
在指定的ingres文件当中声明的url都会跳转到这个地址
nginx.ingress.kubernetes.io/rewrite-target: https://www.123ccc.com:30416
#在指定的ingres文件当中声明的url都会跳转到这个地址原文地址:https://blog.csdn.net/qq_51506982/article/details/135678415
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。
如若转载,请注明出处:http://www.7code.cn/show_58634.html
如若内容造成侵权/违法违规/事实不符,请联系代码007邮箱:suwngjj01@126.com进行投诉反馈,一经查实,立即删除!